Prerequisites
- Configure External URL for your Bytebase instance
- Set up an OAuth 2.0 or OIDC SSO provider in Bytebase
IdP-initiated flow in Bytebase works with OAuth 2.0 and OpenID Connect (OIDC) protocols. This feature uses a specialized endpoint to initiate the authentication flow from the identity provider’s side.
Configuration
Step 1: Configure SSO Provider in Bytebase
First, ensure you have already configured your SSO provider (OAuth 2.0 or OIDC) in Bytebase following the respective documentation:Step 2: Get Your IdP-Initiated URL
Once your SSO provider is configured, the IdP-initiated flow URL follows this format:{EXTERNAL_URL}is your Bytebase external URL (e.g.,https://bytebase.example.com){IDENTITY_PROVIDER_ID}is the Identity Provider ID you specified when creating the SSO provider in Bytebase
https://bytebase.example.com and your Identity Provider ID is okta-company, the IdP-initiated URL would be:
Step 3: Add Deep Linking (Optional)
You can optionally specify where users should land after authentication by adding arelay_state parameter. If not provided, users will be directed to the Bytebase homepage after successful authentication.
The
relay_state parameter is optional. When used, it must be a relative path (starting with /). External URLs are not permitted for security reasons.Okta Configuration
After setting up your OIDC SSO provider in Bytebase, configure the Initiate Login URL in your Okta application to enable IdP-initiated flow.- In your Okta Admin Console, go to Applications > Applications.
- Select your existing Bytebase OIDC application (the one you created when setting up OIDC SSO).
- Go to the General tab and click Edit in the General Settings section.
-
Set the Initiate login URI to your Bytebase IdP-initiated URL:
Where
okta-companyis the Identity Provider ID you configured in Bytebase.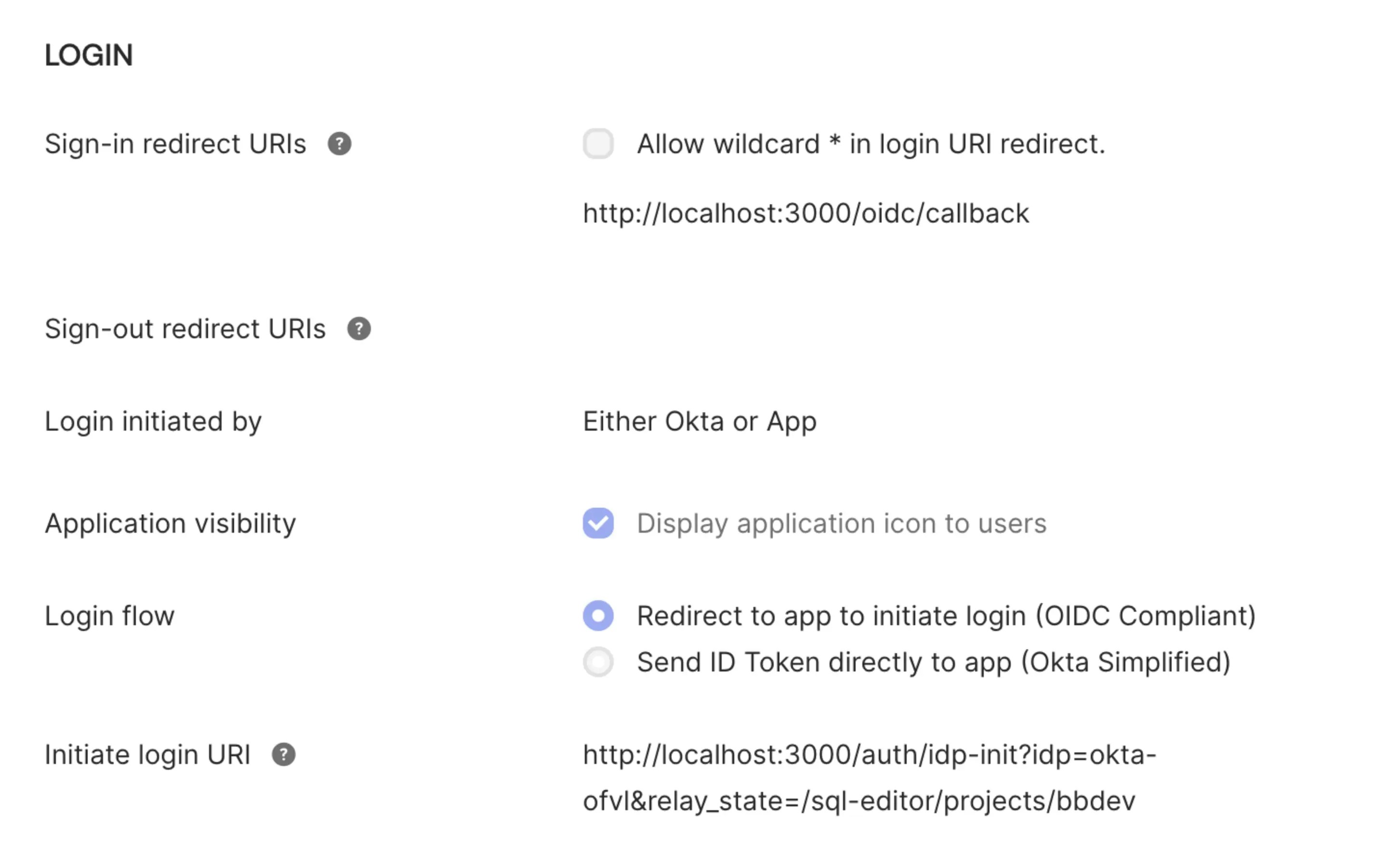
- Click Save to apply the changes.
- Now when users click the Bytebase tile in their Okta End-User Dashboard, they will be automatically authenticated and redirected to Bytebase without needing to click any additional login buttons.
Other Identity Providers
For other identity providers (GitLab, Keycloak, Casdoor, etc.), the configuration typically involves:- Creating a bookmark/shortcut application in your IdP
- Setting the target URL to your Bytebase IdP-initiated URL
- Assigning the bookmark to appropriate users or groups
Security Considerations
IdP-initiated flow in Bytebase includes several security measures:CSRF Protection
The IdP-initiated flow uses the same state parameter mechanism as SP-initiated SSO to prevent Cross-Site Request Forgery (CSRF) attacks. Each authentication request generates a unique, single-use state token.Token Expiration
State tokens expire after 10 minutes, limiting the window for potential replay attacks.Relay State Validation
Therelay_state parameter is validated to ensure it’s a relative path, preventing open redirect vulnerabilities. External URLs are rejected.
Existing Session Handling
If a user already has an active Bytebase session when using IdP-initiated flow, the system will respect the existing session state.Troubleshooting
Users redirected to homepage instead of intended destination
If you’re using therelay_state parameter but users are landing on the homepage:
- Verify that the
relay_statevalue is URL-encoded if it contains special characters - Ensure the path starts with
/(e.g.,/projects/123, notprojects/123) - Check that the path exists and is accessible to the authenticated user
IdP-initiated flow not working
If clicking the application tile in your IdP dashboard doesn’t authenticate users:- Verify your External URL is configured correctly in Bytebase
- Check that the Identity Provider ID in the Initiate Login URI matches exactly what you configured in Bytebase (case-sensitive)
- Ensure the OIDC SSO provider is properly configured and tested using SP-initiated flow first
- Verify the Initiate Login URI is correctly set in your Okta application’s General Settings
Authentication succeeds but shows an error
This may indicate an issue with token exchange or user provisioning:- Verify the OAuth/OIDC configuration in Bytebase has correct client ID and secret
- Check the user information field mapping in your SSO configuration
- Review Bytebase server logs for detailed error messages
- Ensure the user’s email in the IdP matches a valid email format

