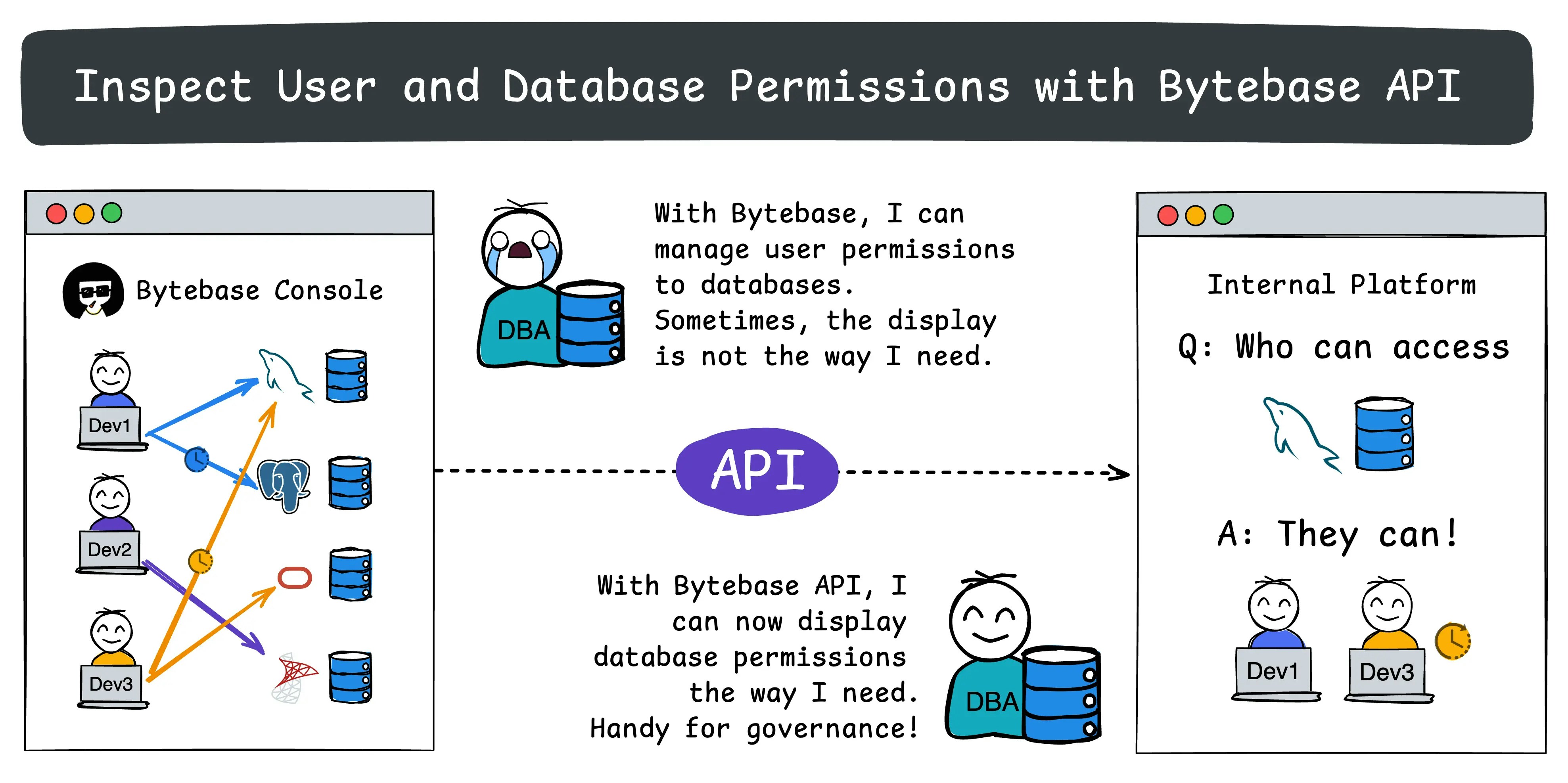
- Set up and configure API access.
- For a given database, which users have been granted permissions?
- For a given user, which databases have been granted permissions?
Repository
https://github.com/bytebase/example-api/tree/main/permission-checkPrerequisites
- Docker installed
- Node.js >= v18
Start Bytebase
Make sure your Docker daemon is running. Copy and paste the commands to start Bytebase.localhost:8080. Register the first admin account which will be granted Workspace Admin.
Create Service Account
-
Log in as
Workspace Admin, and go to IAM & Admin > Users & Groups. Click + Add User, fill in withapi-sample, choose theWorkspace DBArole sufficient for this tutorial and click Confirm.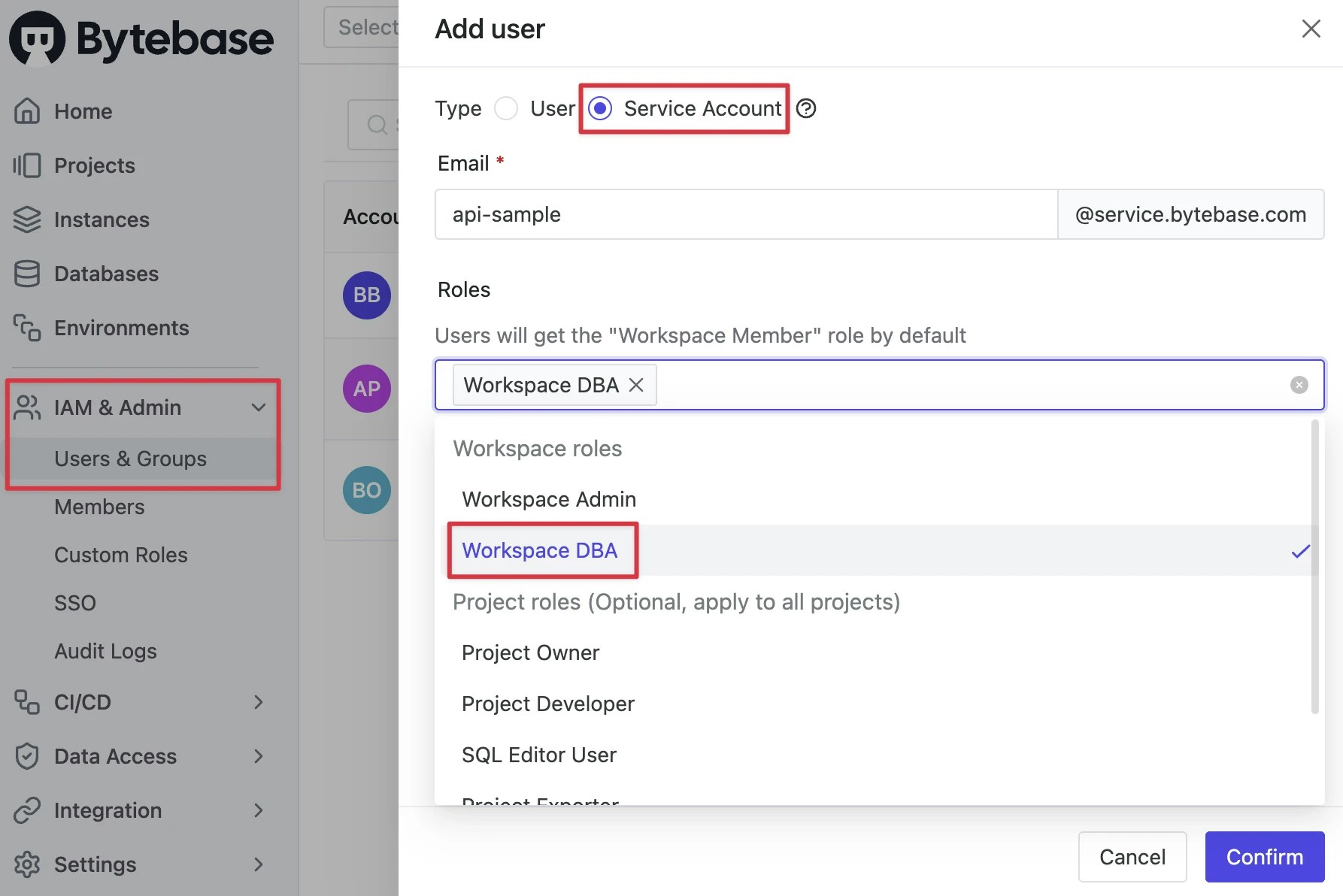
-
Find the newly created service account and Copy Service Key. We will use this token to authenticate the API calls.
Run Demo
- Go to Bytebase API Example repo and clone it.
-
Copy
env-template.localto.env.local.Update the variables.NEXT_PUBLIC_BB_URL:http://localhost:8080NEXT_PUBLIC_BB_SERVICE_ACCOUNT:api-exampleNEXT_PUBLIC_BB_SERVICE_KEY: service key copied in previous step
-
Go to subfolder
permission-check, and run the following commands to start the demo application. -
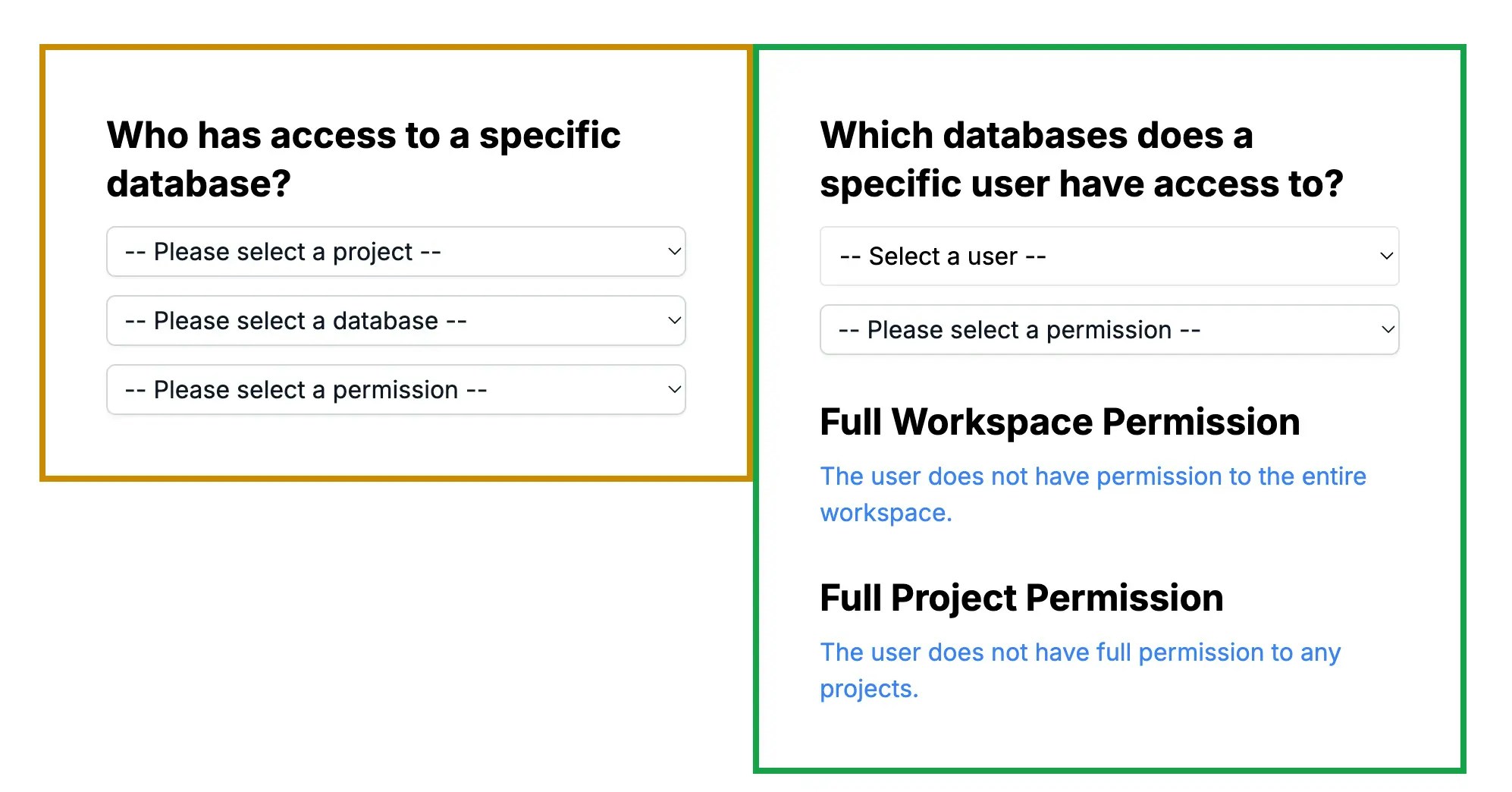
Open the demo in your browser, you’ll see the following page.
-
To enhance the demo’s realism, go to Bytebase and add more users and set up user permissions:
- Add new users in Security & Policy > Users & Groups
- Grant roles:
- For workspace-level access: Security & Policy > Members & Roles
- For project-specific access: Navigate to a project and use Manage > Members
Inspect Permissions
Database + Permission => Users
The left side form demonstrates a scenario where you have a database and want to inspect who has access to it. This is useful for continuously tracking access to sensitive databases and ensuring only authorized users have permissions.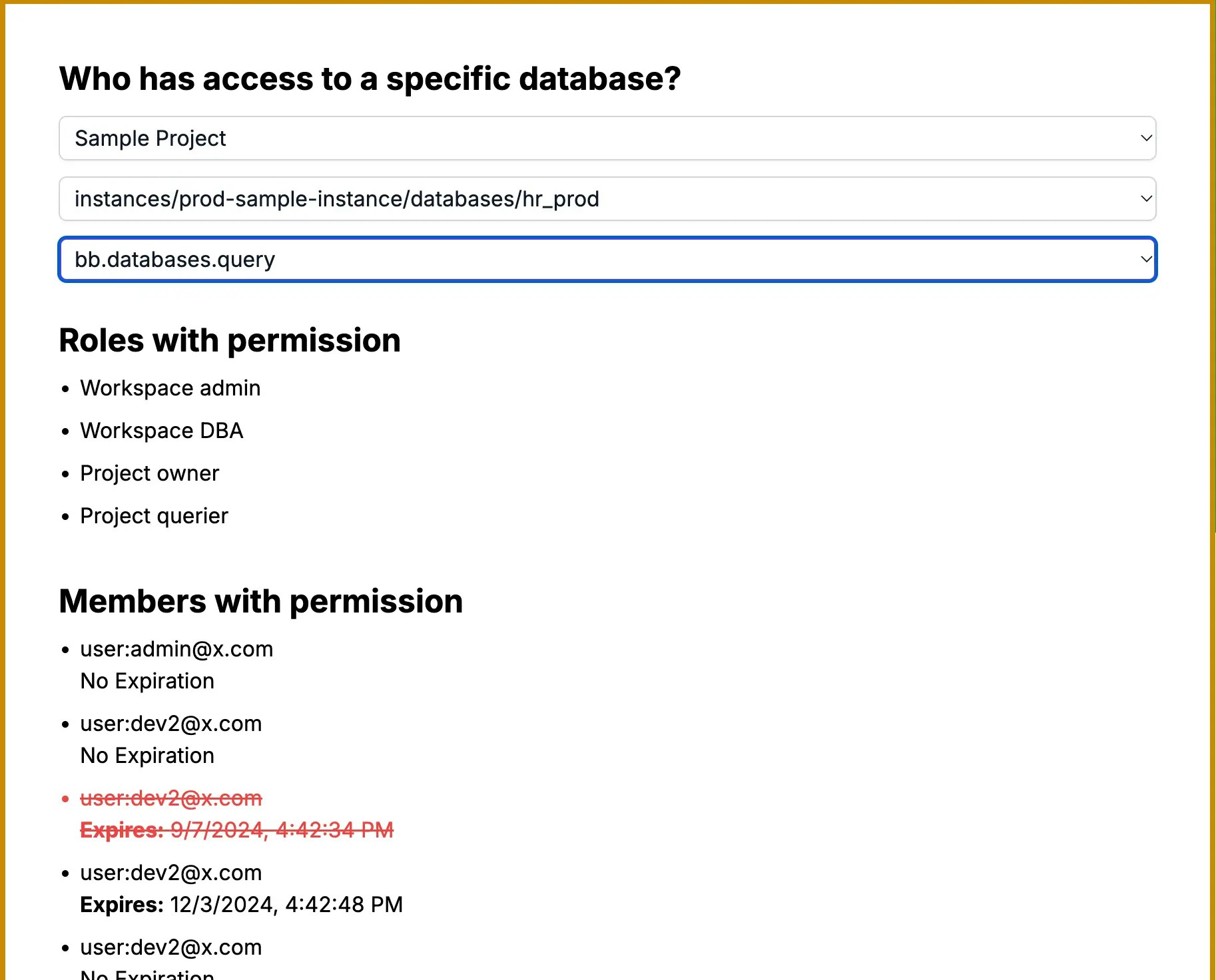
-
In
page.tsx, we fetch all roles by calling the /v1/roles API before any user selection. -
In
db-fetch-user-permission.tsx, after the user selects a project, database, and permission, we filter the roles with the given permission: -
Bytebase has two levels of Identity Access Management (IAM): Workspace and Project. We fetch both:
- Workspace-level IAM: /v1/workspaces/*:getIamPolicy API
- Project-level IAM: /v1/projects/PROJECT_ID:getIamPolicy API
-
We compare the roles with the given IAM to find matches:
-
Some project-level IAM objects include a
conditionfield for fine-grained access control. For example:This grants theSQL Editor Userrole only for thehr_testdatabase intest-sample-instance. -
When processing IAM policies, handle CEL (Common Expression Language) format conditions carefully. In this demo, we parse these conditions using a custom
parseCelExpressionfunction:This functionparseCelExpression, adapted from Bytebase’s CEL plugin and cel.ts, parses the condition expression string. It is primarily based on theconvertFromCELStringfunction in cel.ts, though you could useconvertFromExprto create your own. The function returns an array of database resources with their associated expiration times. This function and related CEL parsing logic are implemented in a customplugins/celfolder within the demo project. -
We then check if the conditions are met for the specific database:
-
The
membersarray may include both users and groups. To handle groups, use the v1/groups API:
User + Permission => Databases
The right side form demonstrates a scenario where you have a user and want to inspect which databases they have access to. This is useful for ongoing tracking of user permissions, especially when roles change or users leave the company.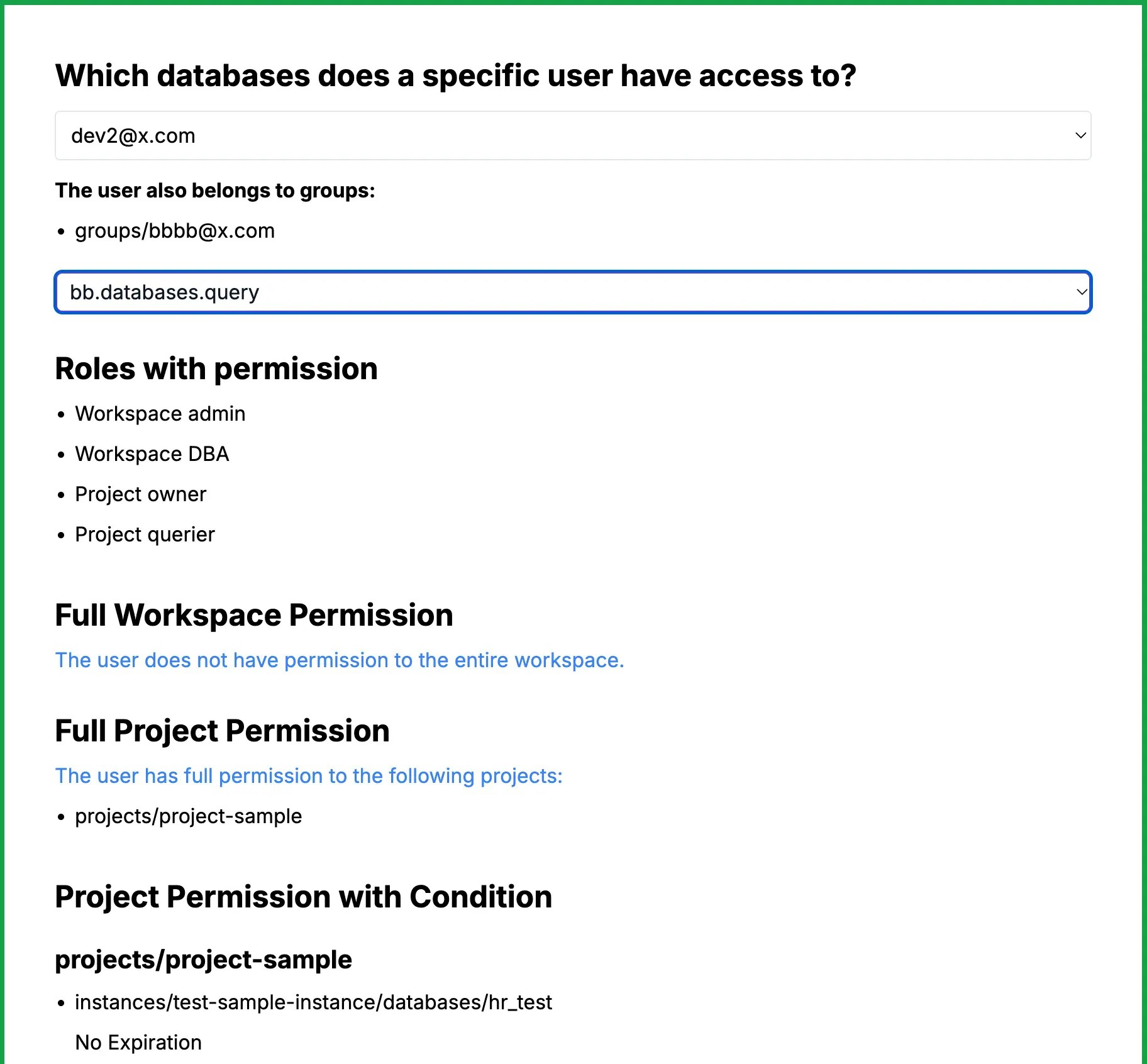
-
Fetch all roles using the /v1/roles API in
page.tsx. -
In
user-fetch-db-permission.tsx, filter roles based on the selected permission: -
Fetch and compare workspace-level and project-level IAM policies:
- Workspace-level check:
- Project-level check:
-
Handle CEL conditions:
-
Group should be taken into consideration too.
Summary
Congratulations! You’ve successfully created a user and database permission inspection tool using the Bytebase API. This allows you to:- Inspect which users have access to specific databases.
- Inspect which databases a particular user can access.

