The tutorial uses Amazon Aurora, while the same approach can be applied to Amazon RDS and other database engines as well.
AWS IAM Auth
For Amazon Aurora and RDS, AWS IAM authentication provides a solution by enabling temporary, secure access without the need for password rotation. With IAM Auth:- Short-lived tokens: Instead of using a static password, a temporary authentication token is generated via AWS SDK or CLI. These tokens are time-limited (by default, valid for 15 minutes).
- Centralized identity: Access is controlled via IAM policies rather than within the DB itself, letting you use fine-grained IAM policies and leverage AWS’s centralized identity management.
- Eliminates hard-coded passwords: No more storing long-lived passwords in configuration files or environment variables. You simply request a token when you need to connect.
Limitation
There are still limitations with AWS IAM Auth:- Limited DB Engine Support: Only MySQL, PostgreSQL, and Amazon Aurora (MySQL/PostgreSQL-compatible) support IAM auth. Other RDS engines (e.g., SQL Server, Oracle, MariaDB) do not.
-
Separate DB-Level User Management: IAM can control who can connect, but once connected, the user’s DB privileges are still governed by database grants (e.g.,
GRANT SELECT ON …). You can’t manage fine-grained table-level permissions solely through IAM. - Auditing & Visibility Trade-Offs: If you opt for one shared database user for everyone, you lose per-user audit trails inside the DB. Creating one DB user per developer (and possibly per IAM identity) can be cumbersome. You do get detailed auditing but at the cost of more management complexity.
- Complexity with Large Teams & Enterprise Integrations: AWS SSO/Identity Center integration simplifies IAM user management, but you still need a strategy for mapping many developers to DB users (shared vs. individual). For large teams, mapping roles/groups to DB users can become complex.
Bytebase
Bytebase is an open-source database DevSecOps solution that complements AWS IAM Auth:- More DB Engine Support: Bytebase supports MySQL, Postgres, Amazon Aurora as well as other RDS engines (e.g., SQL Server, Oracle, MariaDB).
- Fine-Grained Access via Bytebase: Even if you opt for a shared DB user in Aurora/RDS (e.g. db_iam_dev_user), Bytebase maintains its own user/role model. Each developer logs into Bytebase with their individual identity (integrated with SSO). You can grant database permission at the table level.
- Auditing at the Platform Level: Bytebase tracks exactly which user performed which action, even if the database sees only one shared DB user. This gives you per-user audit trails without the overhead of creating separate Aurora/RDS DB users or separate IAM policies per developer.
Solution Overview
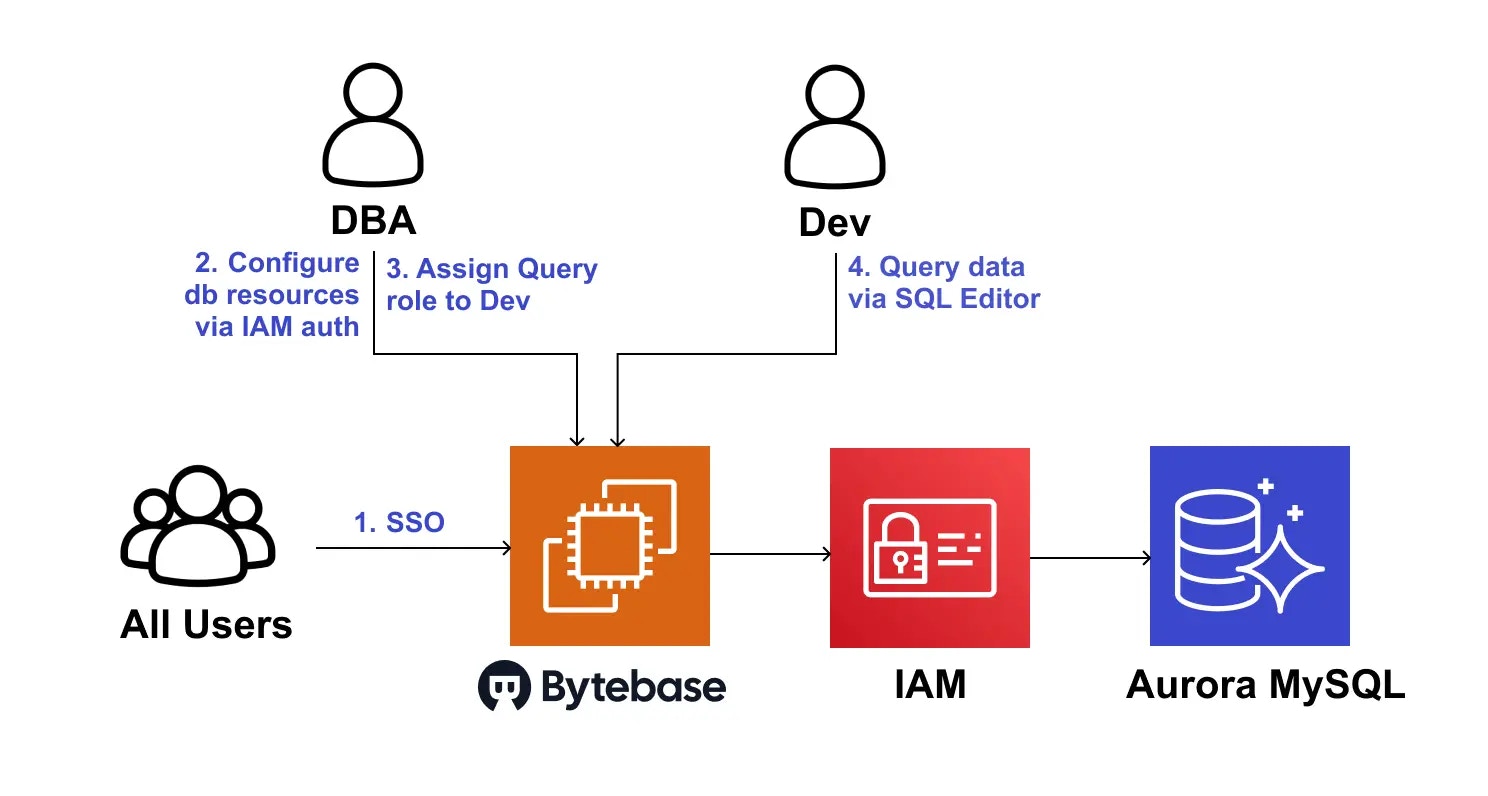
The following architecture shows how Bytebase enables Just-in-Time (JIT) database access for Amazon Aurora: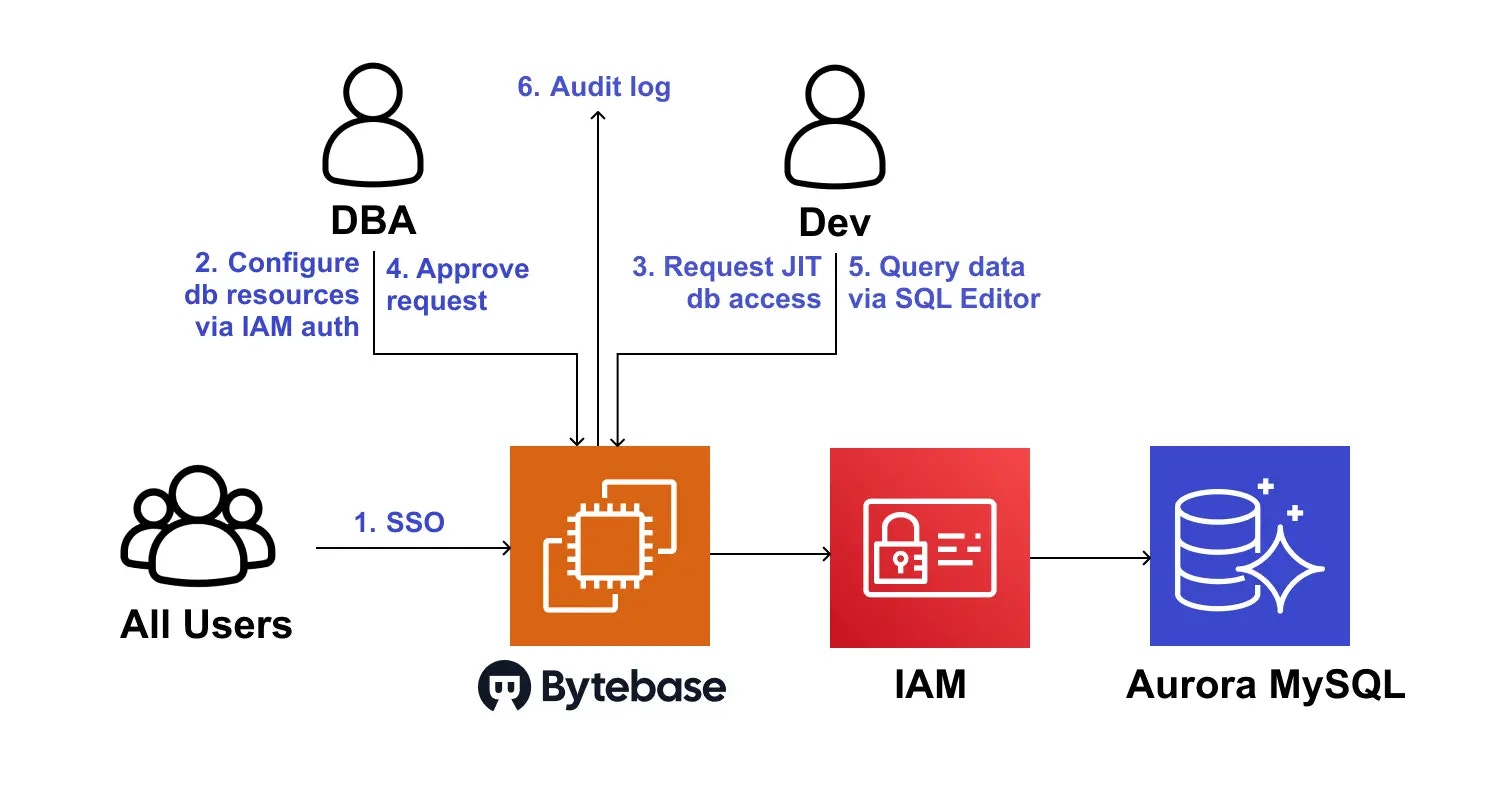
Architecture Components
- Bytebase itself can run under an IAM role that can connect to Aurora/RDS using the shared IAM-based user.
- Developers authenticate to Bytebase with their corporate IdP (via SSO). Developers don’t need to see or store any DB credentials. Each developer’s actions are tracked individually in Bytebase.
JIT Database Access Workflow
- All users can authenticate to Bytebase with their corporate IdP (via SSO).
- DBAs configure Bytebase to connect to your Amazon Aurora MySQL database (Bytebase also supports other RDS engines).
- Developer requests Just-in-Time (JIT) table-level access with an expiration time directly through Bytebase.
- DBAs review the request and approve it.
- Developer can query data via Bytebase SQL Editor.
- The developer’s actions are tracked in Bytebase audit log.
Prerequisites
For this walkthrough, you need the following:- An AWS account
- An AWS Identity and Access Management (IAM) user with permissions to connect to Amazon Aurora
- An EC2 instance with Docker installed
- An Amazon Aurora PostgreSQL database for Bytebase metadata
- An Amazon Aurora MySQL database to be managed by Bytebase
Set up AWS IAM for Aurora MySQL connection
Enable AWS IAM authentication for Aurora MySQL
While creating Aurora MySQL instance, you need to enable AWS IAM authentication.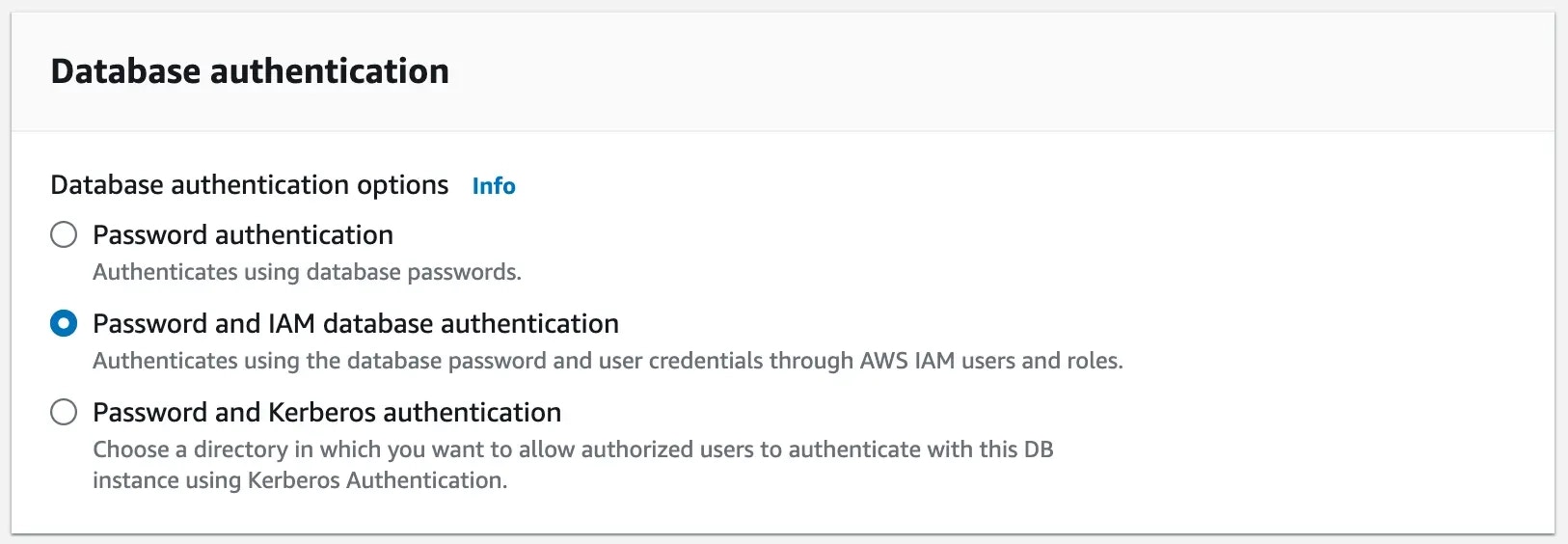
Create IAM policy
- Go to IAM > Policies and click Create policy.
-
Select
RDS IAM Authenticationfor service.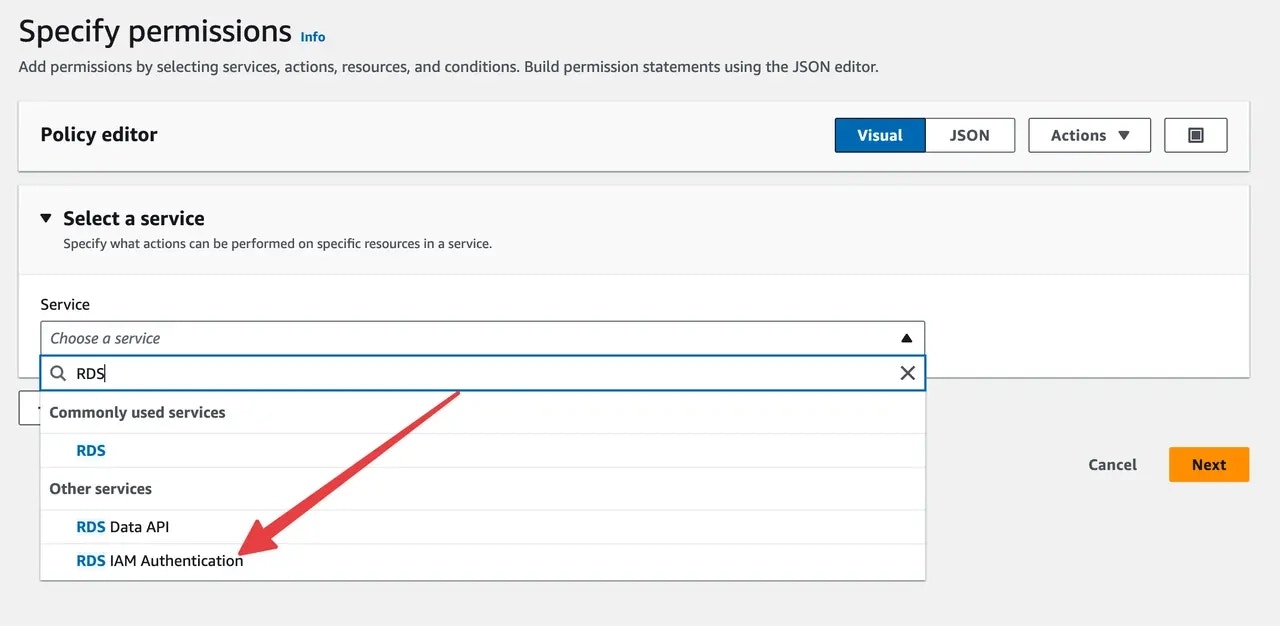
-
Select
connectpermission andspecificas Resource. CheckAny in this account. -
Name it
rds-connectand create this policy.
Create IAM user
-
Go to IAM > Users and click Create user. Name it
rds-connector. -
Choose
Attach policies directlyand selectrds-connectpolicy. Click Next and then click Create user. -
On the user detail page, click Create access key, and choose
Application running on AWS compute serviceas the use case. Because you will run Bytebase in EC2 instance. Click Next. -
Then you can save the
Access key IDandSecret access keyfor later use.
Step 1: Run Bytebase in EC2 instance
-
Connect to the Aurora PostgreSQL instance and create a database
bbfor Bytebase metadata. -
Connect to the EC2 instance and run the following command to start Bytebase. Put your AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, AWS_REGION, PG_URL in the command.
Step 2: Configure Bytebase to Connect to Aurora MySQL via AWS IAM
- The first registration will be granted an admin role. Log in, click Instances on the left bar and click Add instance.
-
Select MySQL as the database type. Fill in the following information and click Create.
- Instance Name:
AWS Aurora MySQL Prod - Environment:
Prod - Host or Socket:
aurora-mysql-instance-prod.ctxxxxxxx5.ap-xxxxx-1.rds.amazonaws.com - Port:
3306 - Connection Method:
AWS RDS IAM - Username:
bytebase - Database Region:
ap-xxxxx-1
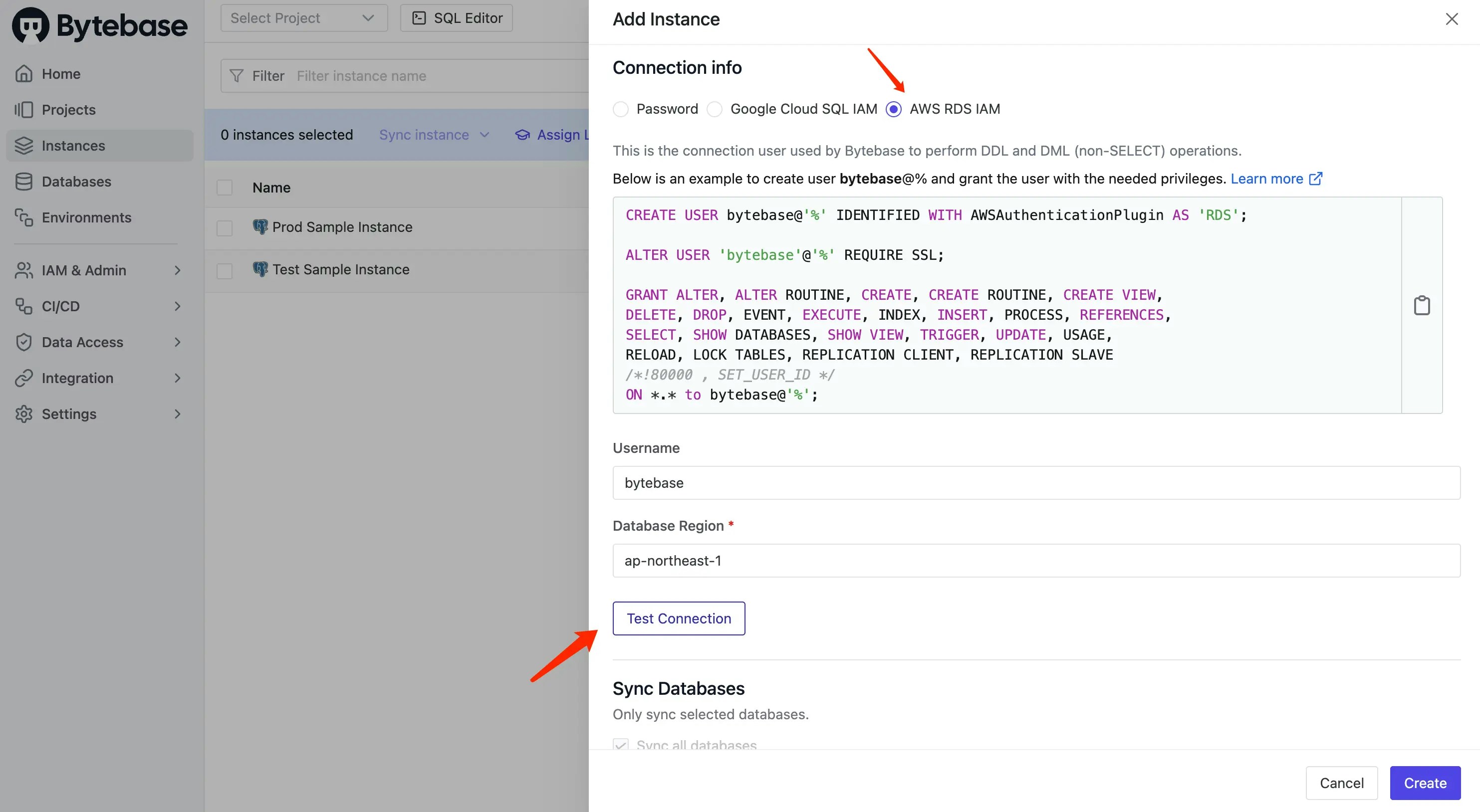
- Instance Name:
-
Click Select Project on the top bar and create a new project
Aurora MySQL Project. - (Optional) If you don’t have any existing databases in the aurora mysql instance, you can check the employee small sample data and import them into the instance first.
-
Click Database > Databases on the left bar, and then click Transfer in DB to transfer in existing databases, for the sample data, it’s
employee. -
Click SQL Editor on the top bar, connect to the
employeedatabase. Double click theemployeedatabase and you’ll see the data.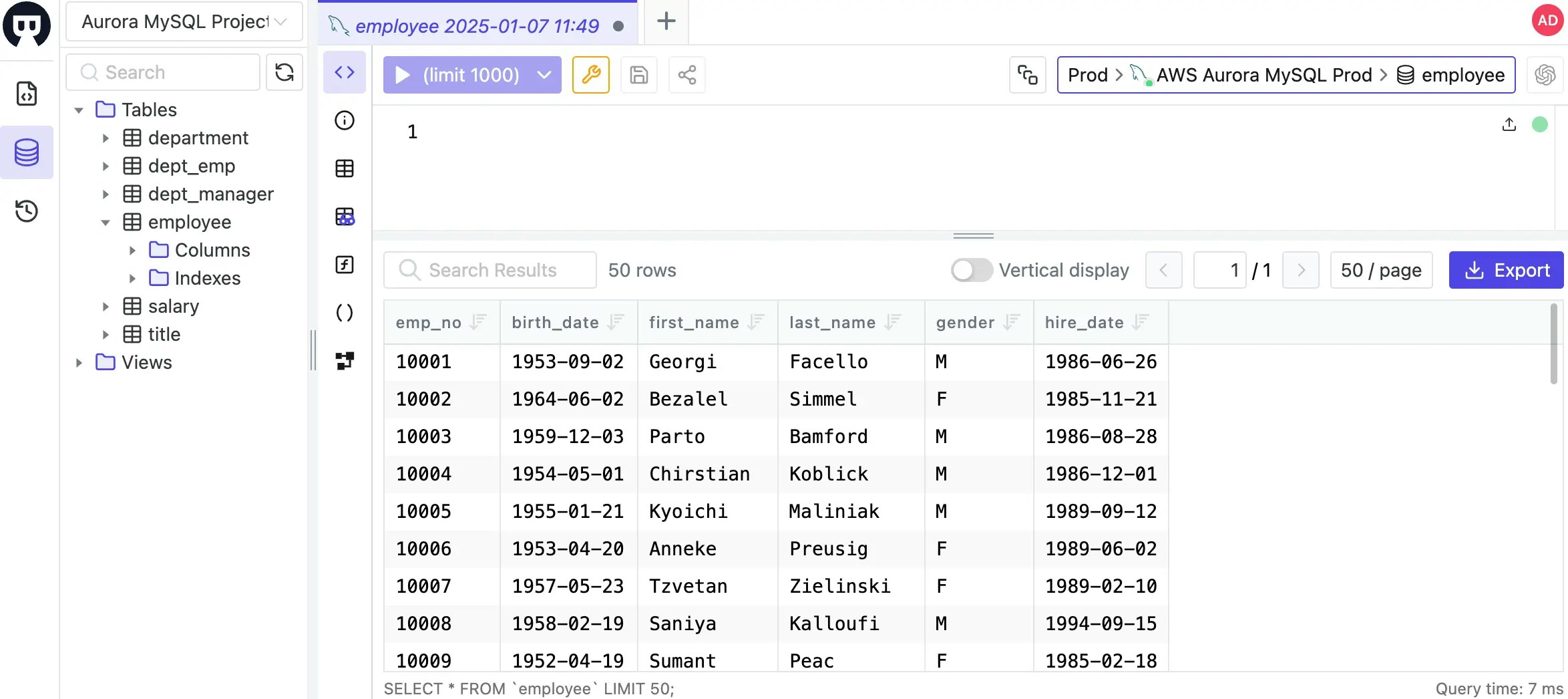
Step 3: Developer requests Just-in-Time (JIT) table-level access through Bytebase
Register a developer
-
By default, the
(workspace) adminhas the full access to the database. Click IAM&Admin > Users&Groups on the left bar, and then click Add user. -
Create a user
devwith the roleProject Developer. This project-level role will be applied to all projects automatically. -
Log in as the user
dev, click Select Project on the top sidebar, and chooseAurora MySQL Project -
Click Database > Databases on the left bar, you should see two database
employee. -
Click SQL Editor on the top bar, connecting to the
employeedatabase is impossible. Because it’s Community Plan.
Admin assigns developer access to the database (Community and Pro Plan)
-
Login as the
adminuser, go intoAurora MySQL Project, click Manage > Members on the left sidebar. -
Click Grant Access, select the developer
dev, select theSQL Editor Userrole, then set 1 day Expiration, and click Confirm button. Here you may notice in Community Plan, you can only set access to all databases in the project.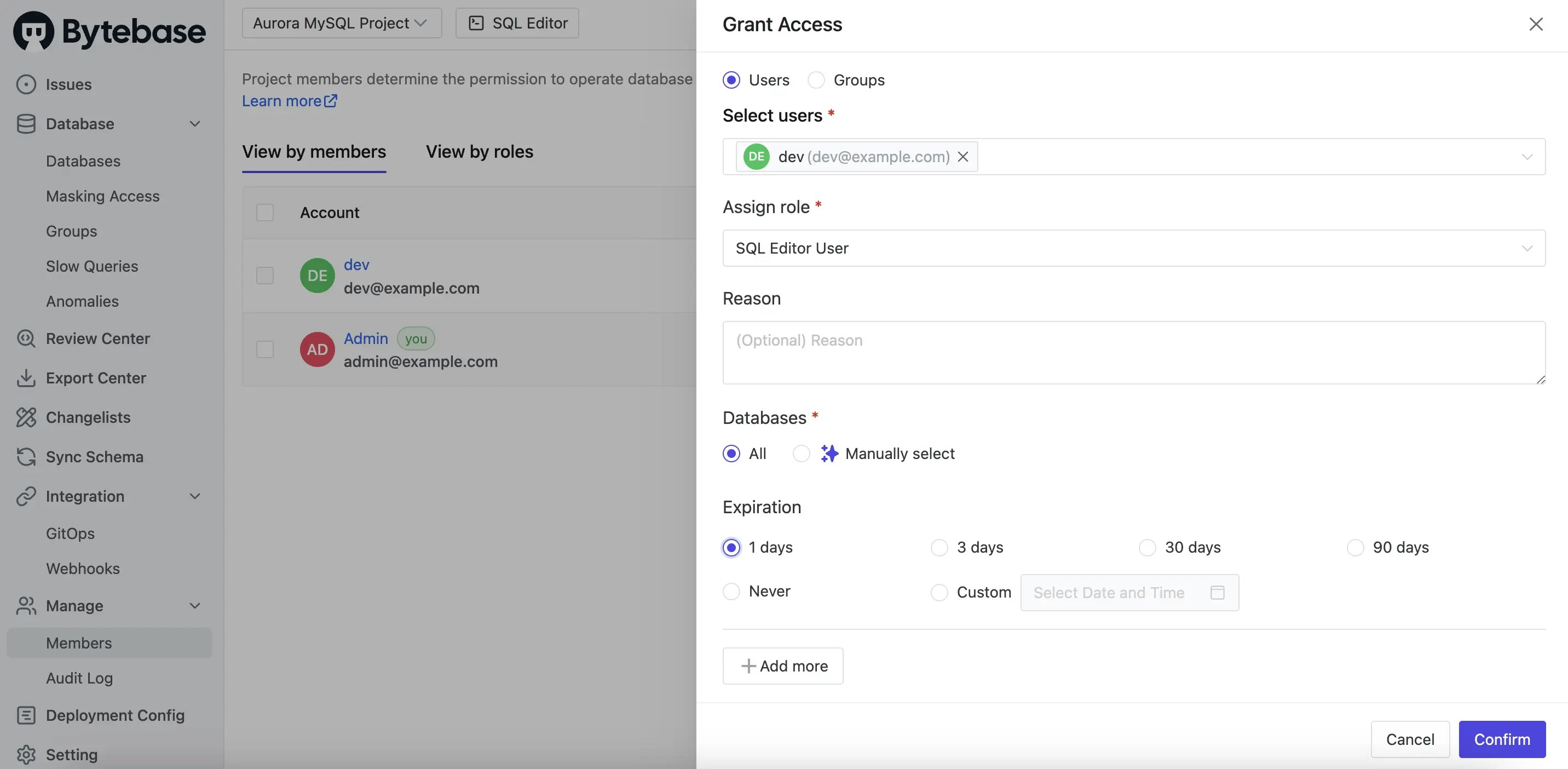
-
After the access is granted, log in as the
devuser again, you now have access to the production database in SQL Editor. After one day, the access will expire automatically.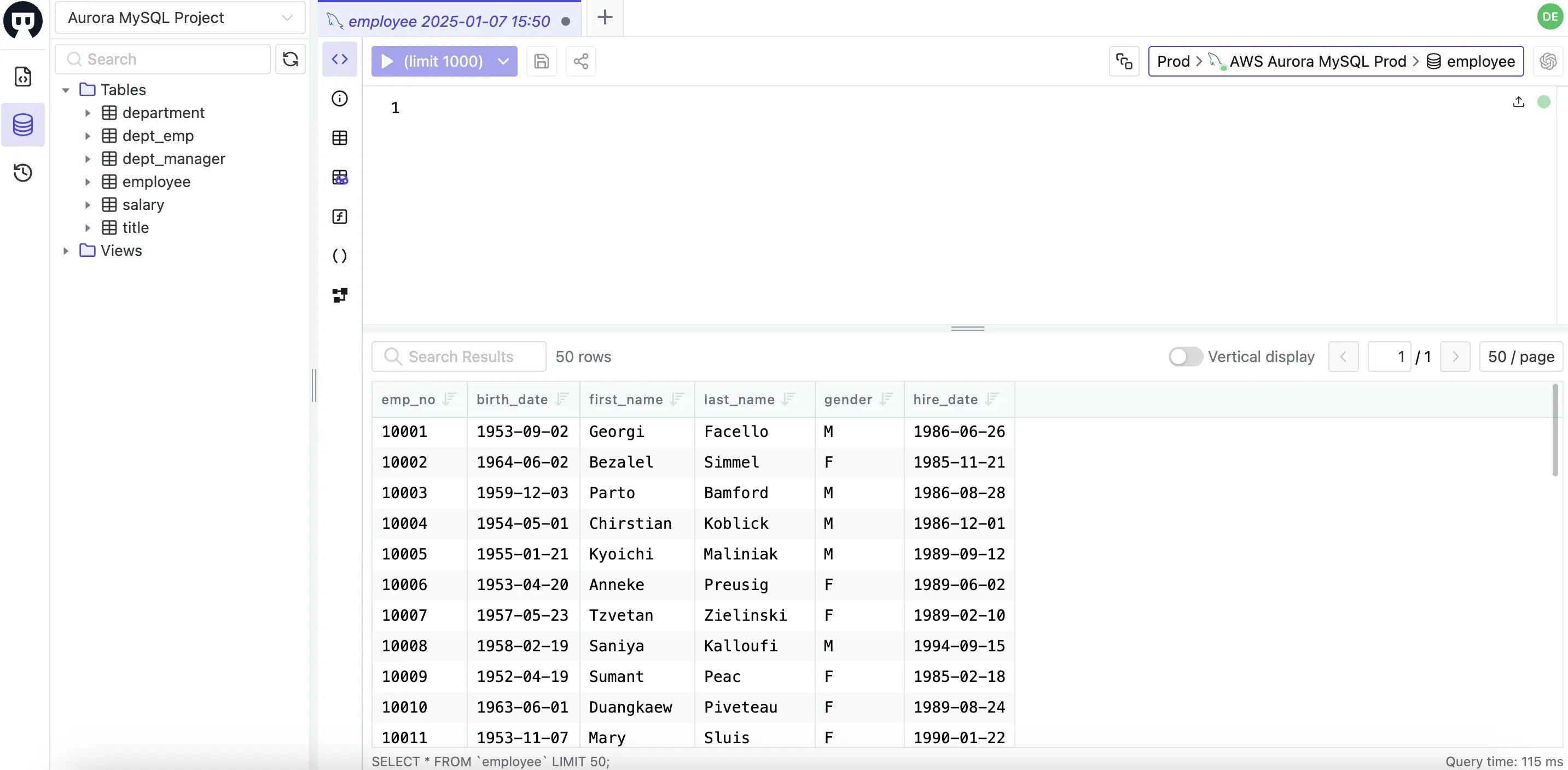
Developer requests JIT access to the database (Enterprise Plan)

-
Login as
adminuser, go intoAurora MySQL Projectand revoke thedevuser’s access to the production database. - Upgrade to the Enterprise Plan. You may request a 14-day trial from here.
-
Click CI/CD > Custom Approval on the left sidebar. Assign licenses to the aurora mysql instance to enable this feature.
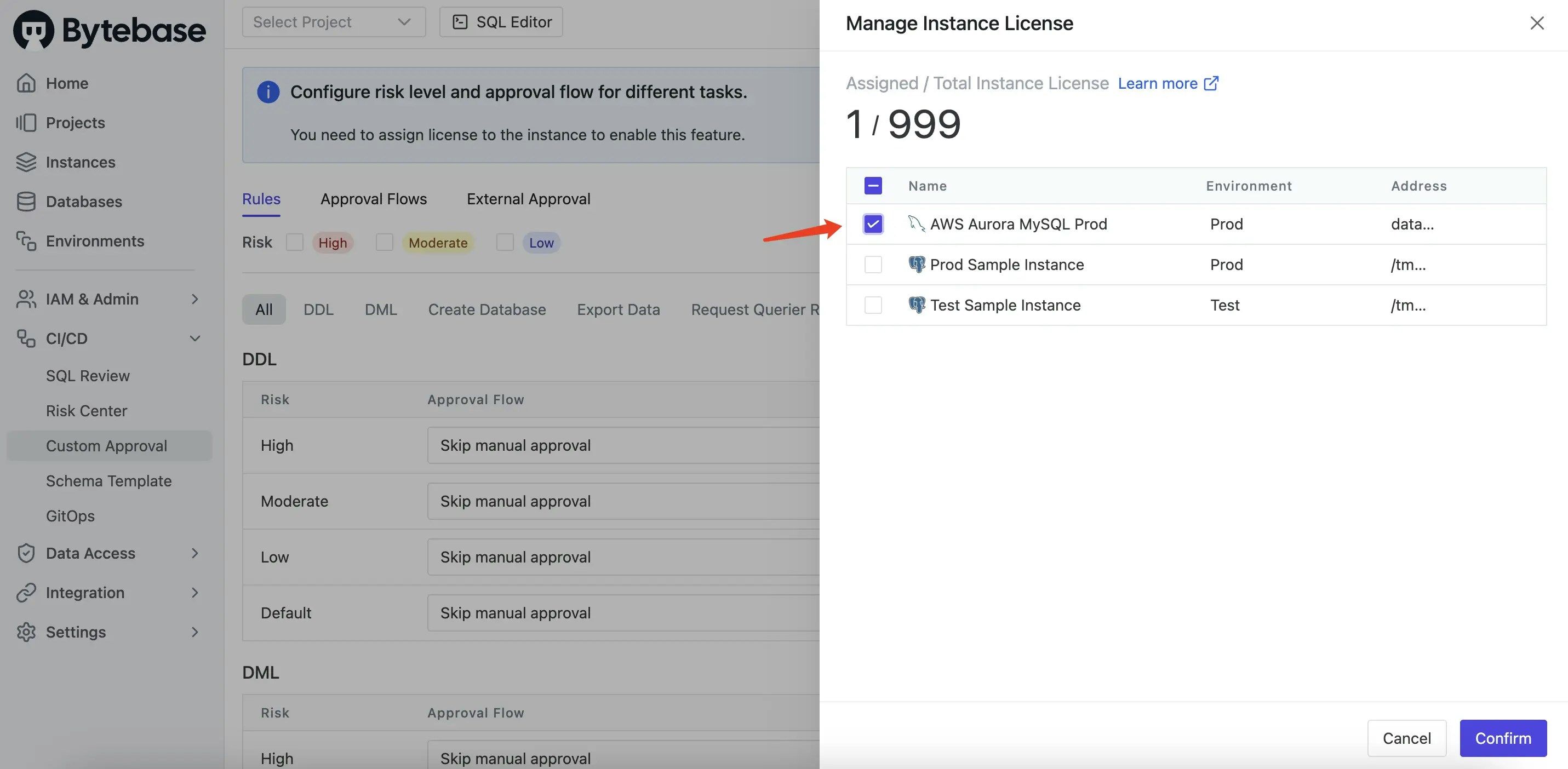
Request Querier Rolewhich triggers when the environment isProd.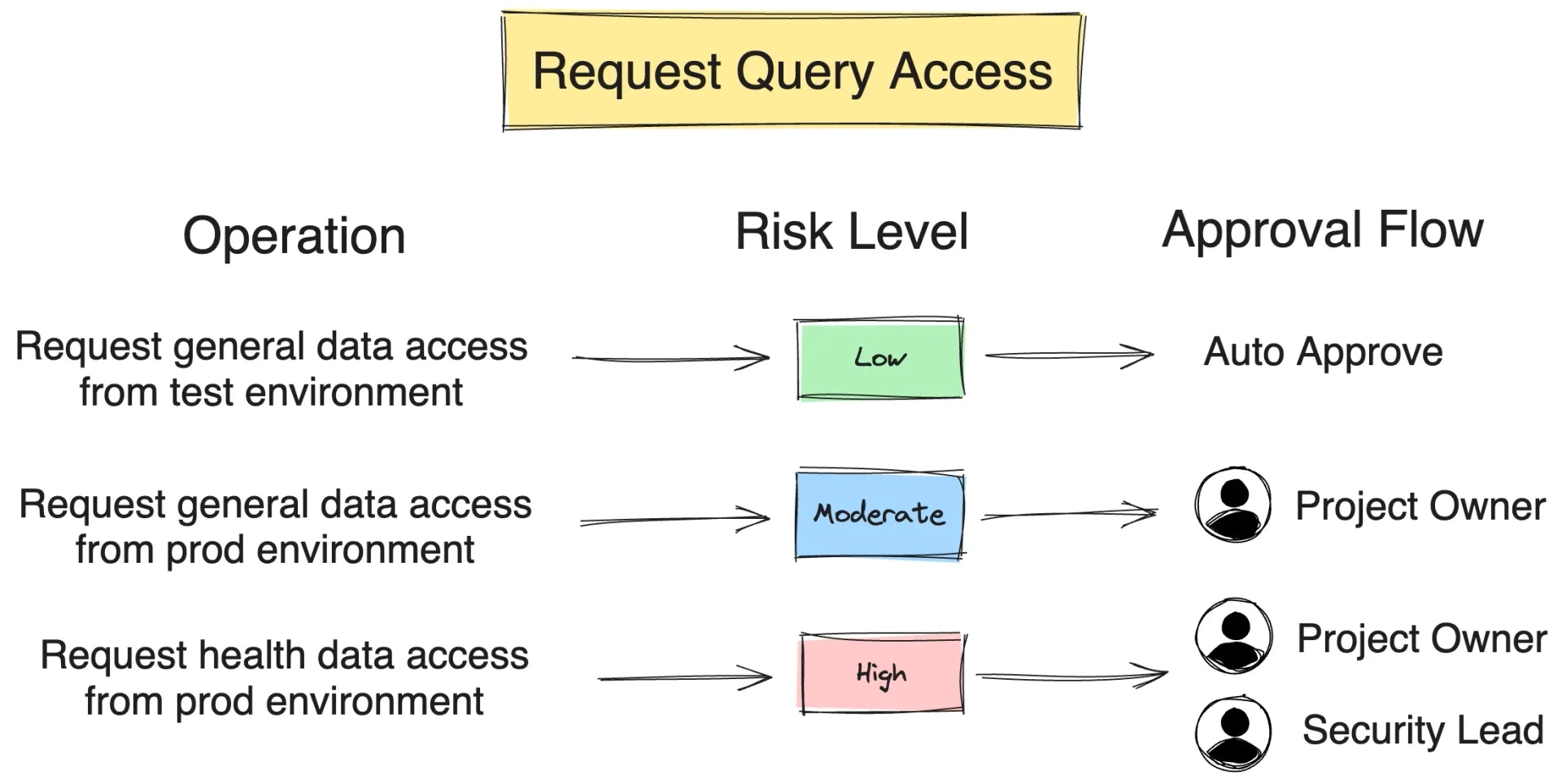
-
Scroll down to Request Querier Role section, add
highrisk an approval flowProject Owner.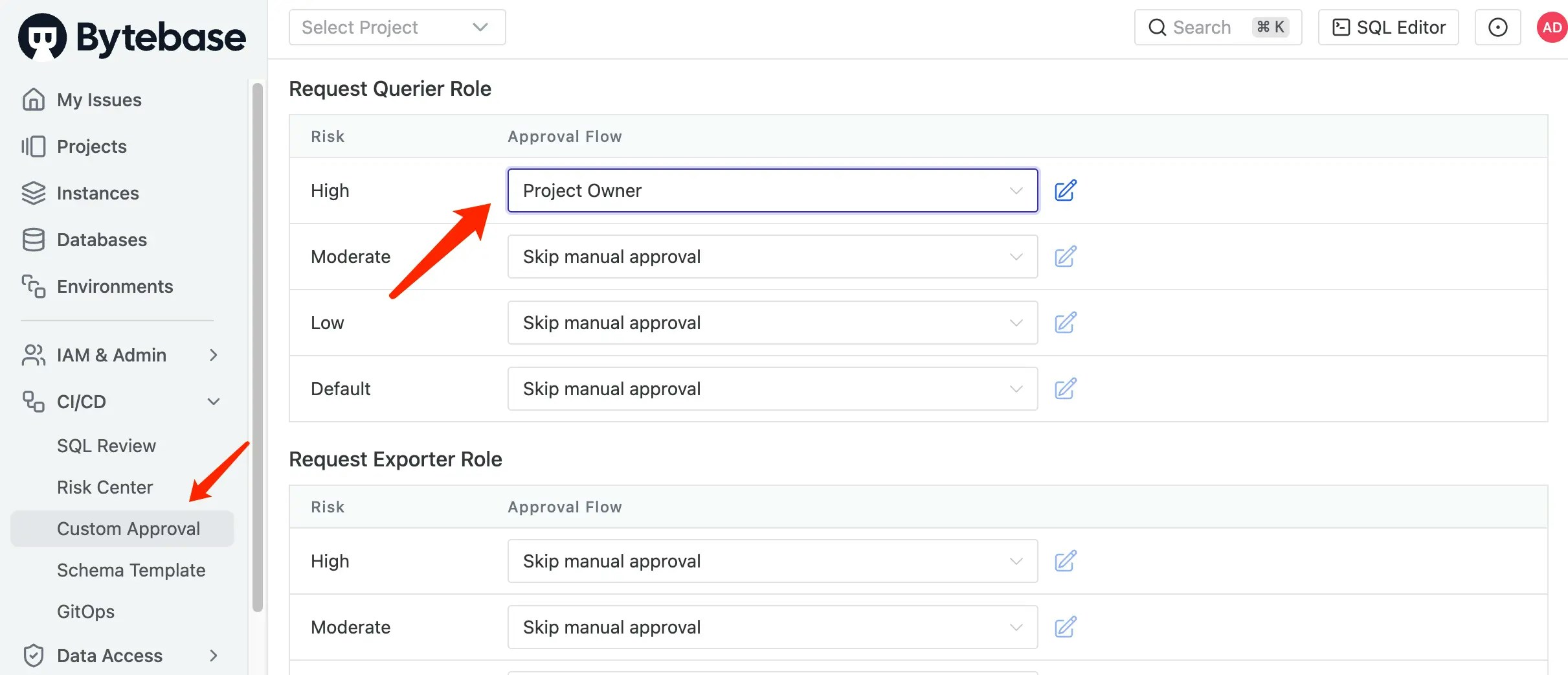
-
Click CI/CD > Risks on the left sidebar. Define a High risk policy for
Request Querier Rolewhich triggers when the environment isProd.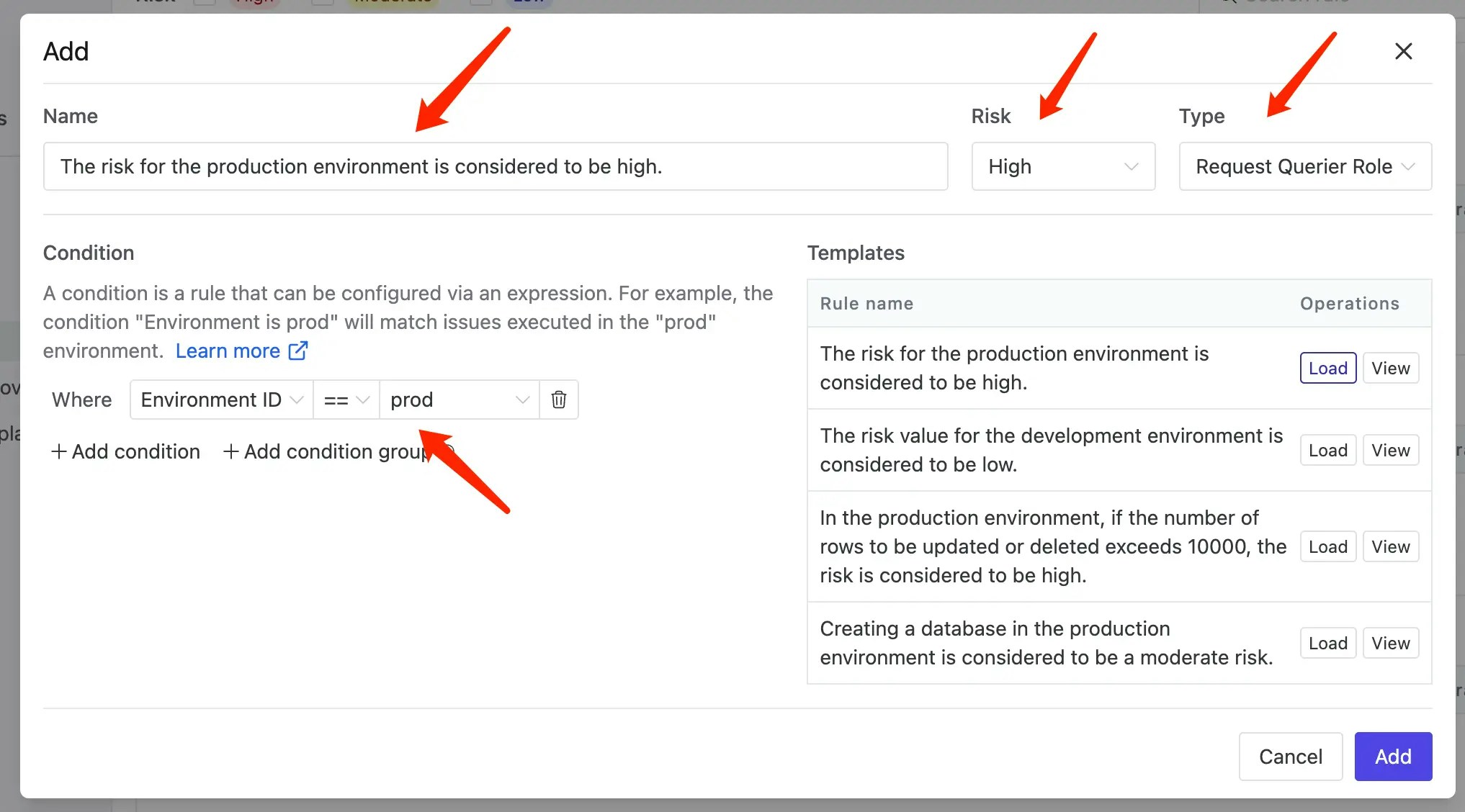
-
Login as the
devuser again, then go to SQL Editor page. Click Connect to a database or Select a database to start. You should see thehr_prodandhr_testdatabases listed, click Request query to request a JIT access.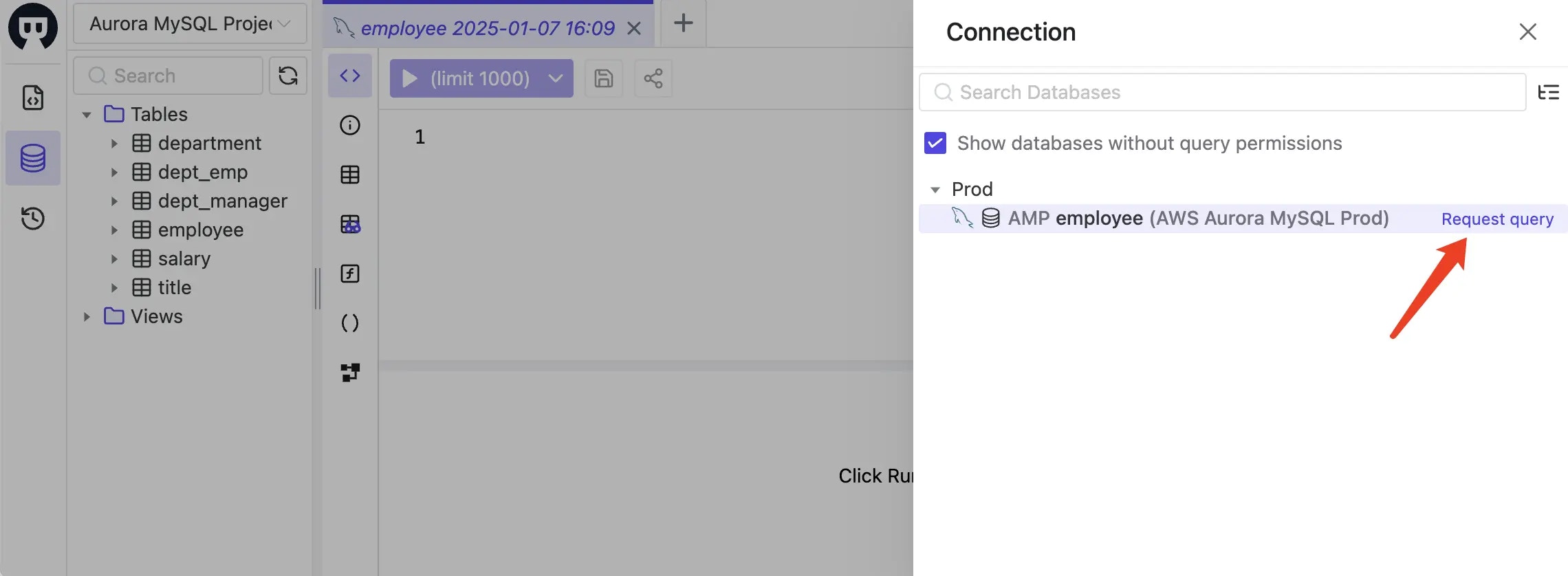
- Another way is to go to Database > Databases page, click Request Querier Role.
-
In the Request Querier Role modal, choose Manually select, then
employeesalaryandtitleunderhr_proddatabase, and click OK button. Here you may also specify the expiration time which can be a specific time, or relative time from now.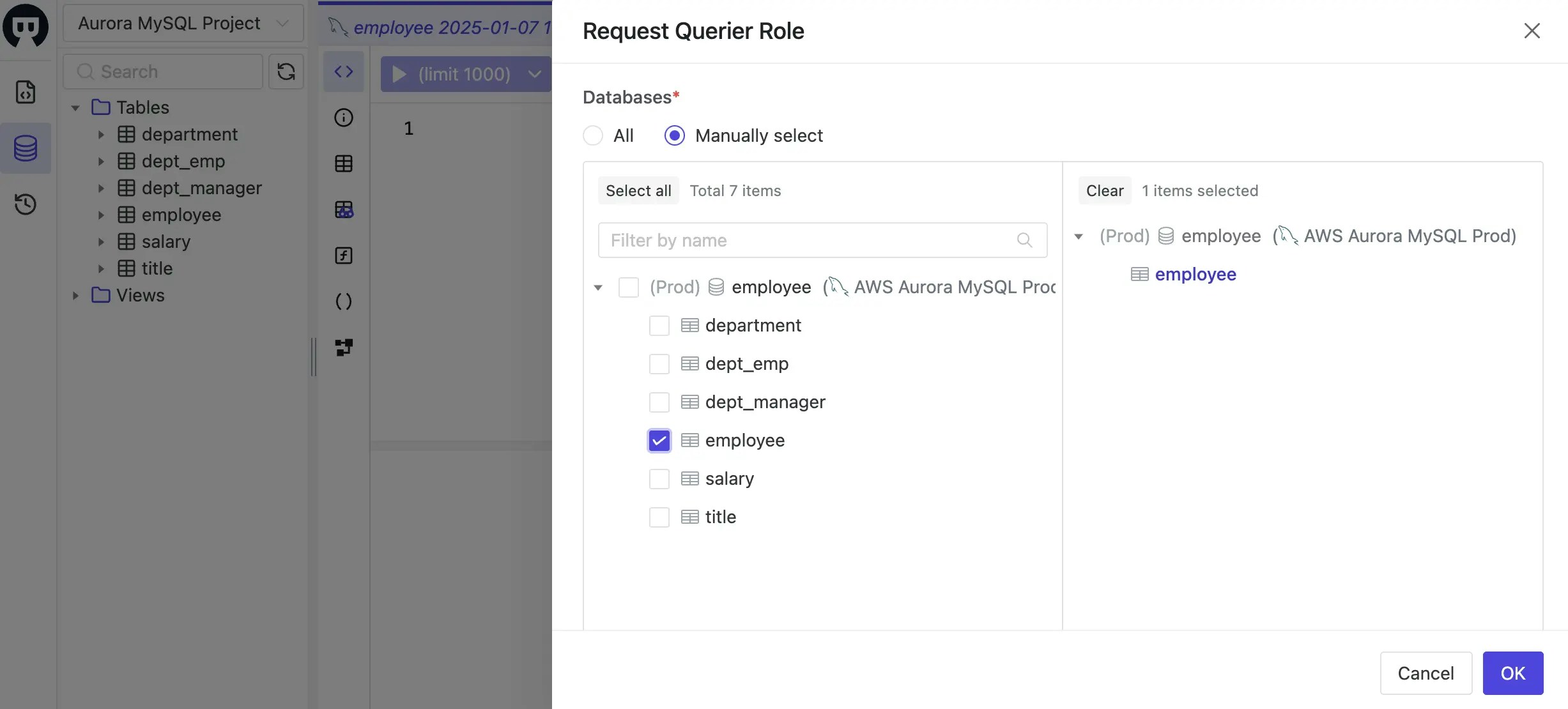
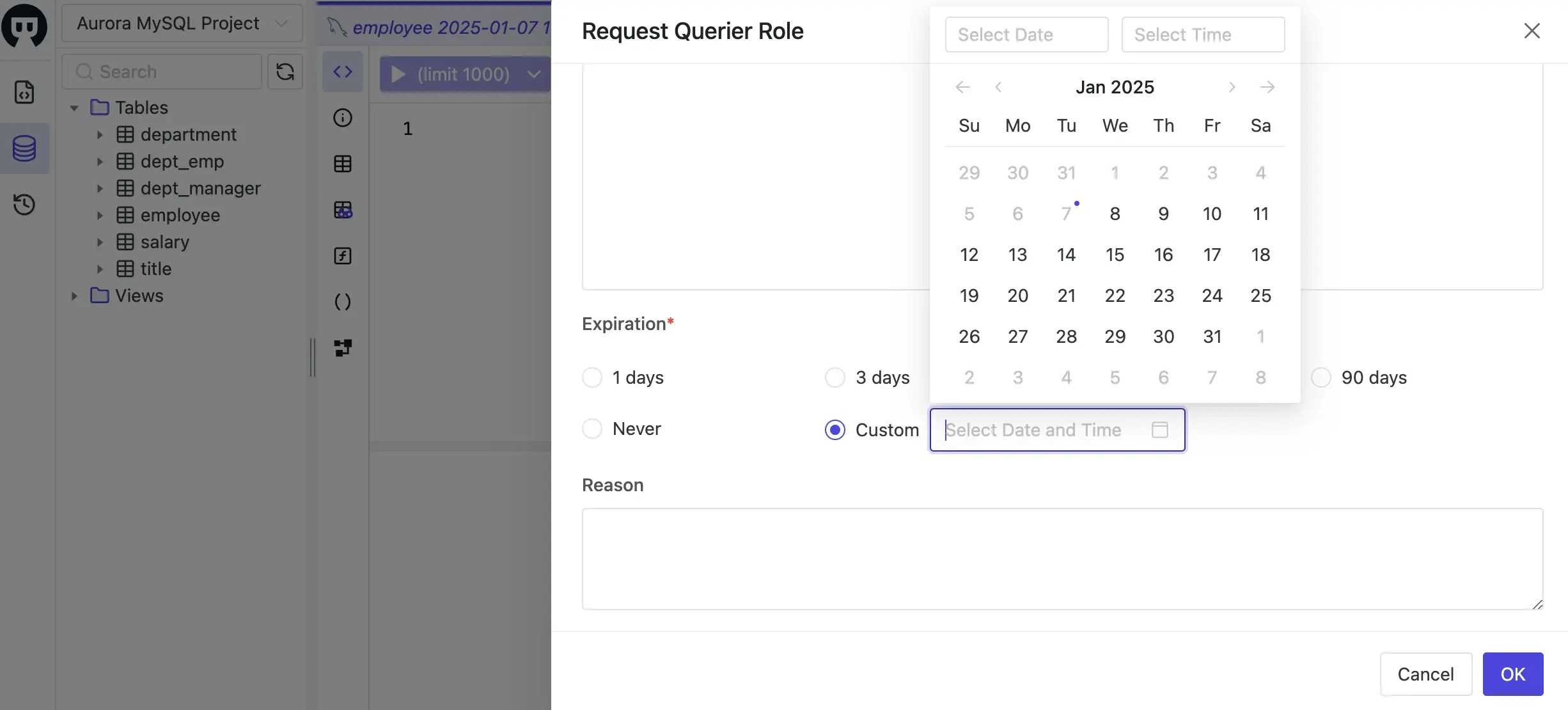
-
An request issue will be created, switch to the project owner (the admin user), go to Issue page, you should see the request issue. Click Approve button to approve the request.
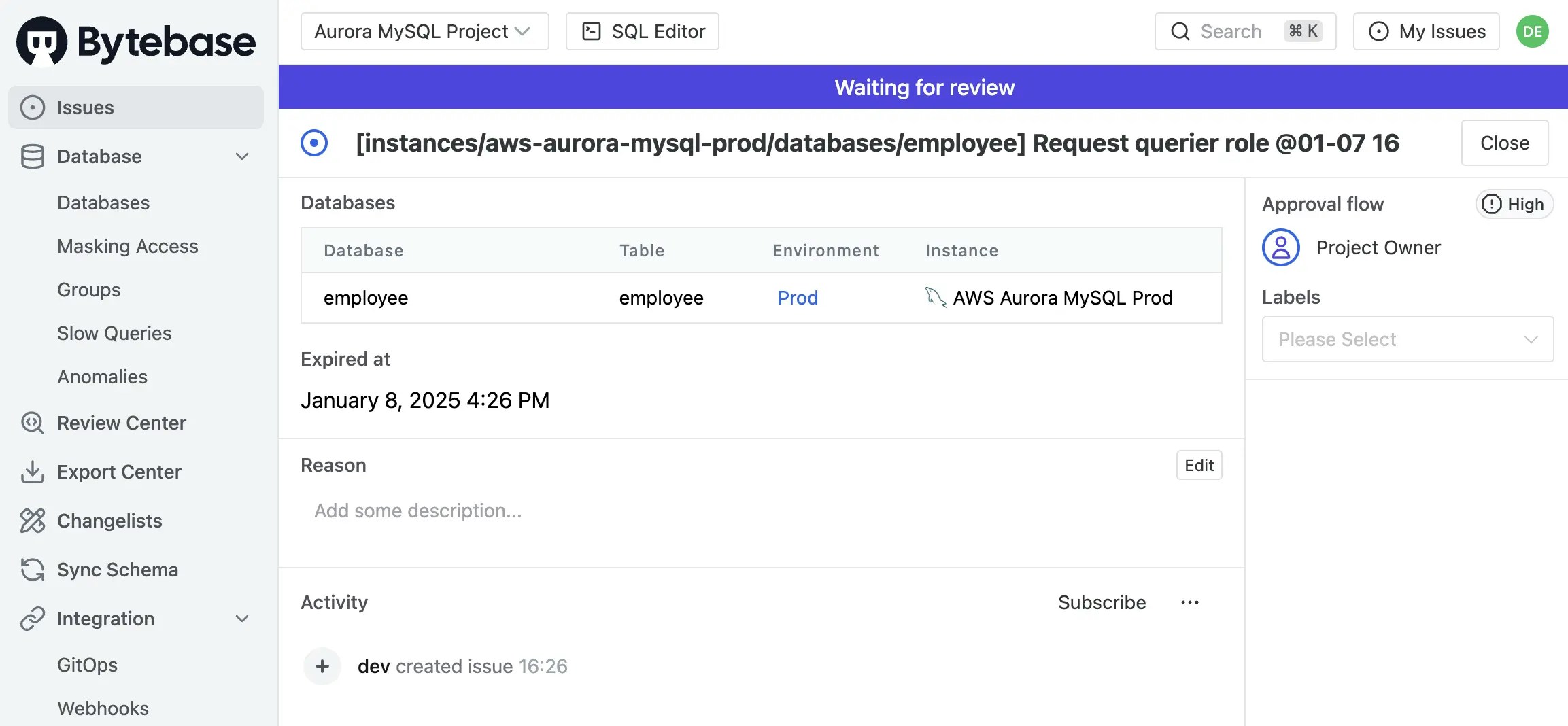
-
Switch back to the
devuser, go to SQL Editor, you should be able to query fromemployeetable. If you query from other tables, you will get errors and suggest to request a JIT access.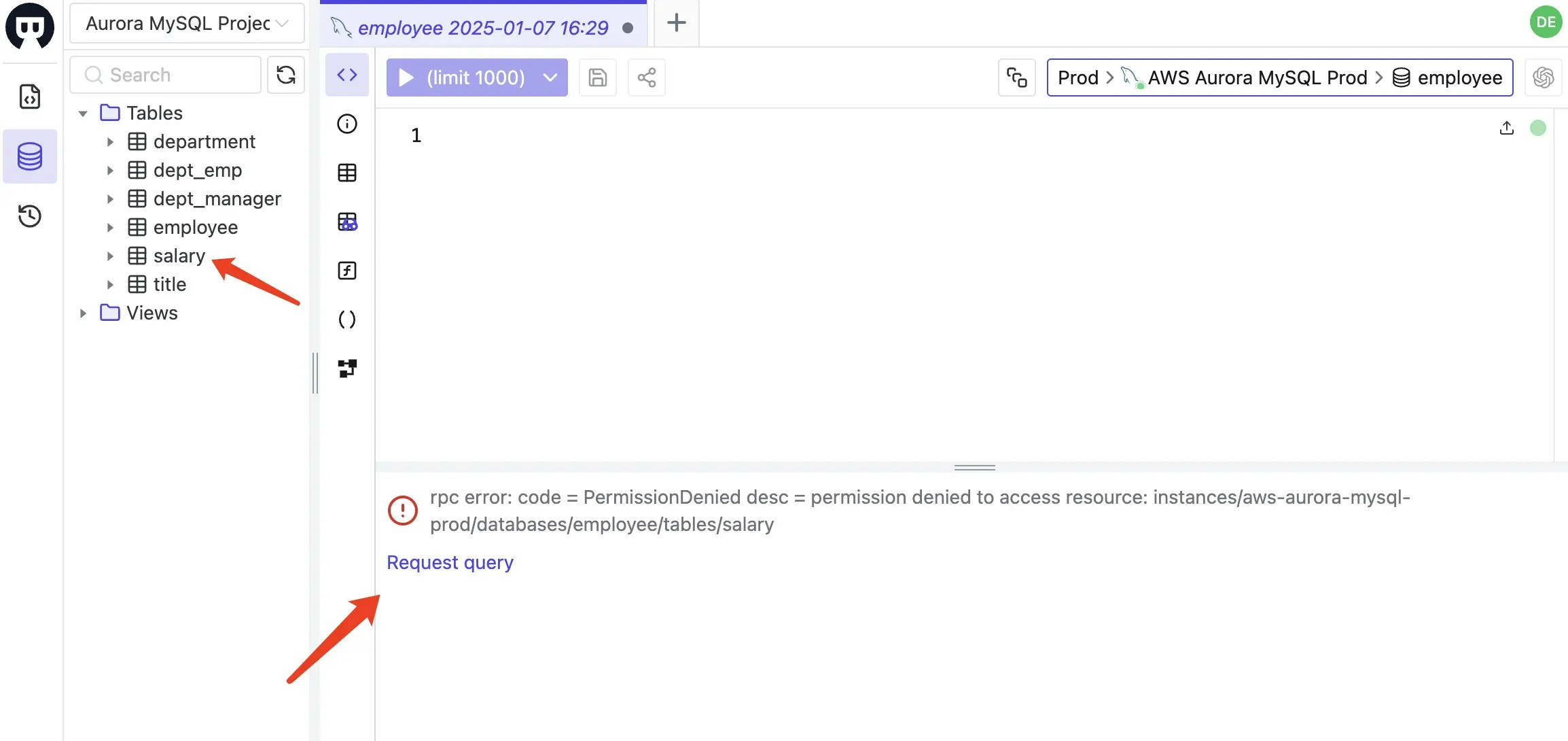
-
After the
devuser get the access, he can solve the incident. The admin user can revoke the access directly from the Manage > Members page or wait for the access expiration. -
adminuser can also check the audit log by clicking IAM&Admin > Audit Log on the left sidebar. The audit log will show all the data access history of thedevuser.

