- Database GitOps with GitHub Actions
- Database GitOps with Azure DevOps Pipeline
- Database GitOps with GitLab CI (this one)
- Database GitOps with Bitbucket Pipelines
This tutorial shows you how to build an database GitOps workflow using GitLab CI and Bytebase API. You’ll learn to create a streamlined database release workflow where you can:
- Submit schema migrations through GitLab
- Automatically run SQL reviews on merge requests
- Auto-create and deploy Bytebase releases when merging to
main
While we use PostgreSQL with GitLab CI in this guide, you can apply these concepts to other SQL or NoSQL databases with any CI platforms like GitHub Actions, Bitbucket Pipelines, or Azure DevOps using the Bytebase API.
Repository
https://gitlab.com/bytebase-sample/gitops-examplePrerequisites
- A Bytebase instance (Bytebase Cloud or self-hosted)
- For self-hosted version, you need Docker to run Bytebase
Automatic Rollout across environments
Step 1 - Set up Bytebase
- Cloud
- Self-Hosted
Use Bytebase Cloud for instant setup without infrastructure management. CI/CD services can connect immediately.Best for: Quick testing, evaluation, and small teams
Step 2 - Create Service Account
-
Log in as
Workspace Admin, and go to IAM & Admin > Users & Groups. Click + Add User, fill in withapi-sample, and assign theWorkspace MemberandGitOps Service Agentroles, which are sufficient for this tutorial, then click Confirm. -
Find the newly created service account and Copy Service Key. We will use this token to authenticate the API calls.
Step 3 - Configure SQL Review in Bytebase
Since you will need to run SQL review on your PRs, you need to configure the SQL review in Bytebase.- Go to CI/CD > SQL Review, click Create SQL Review.
-
Select the
Sample Templateand click Next.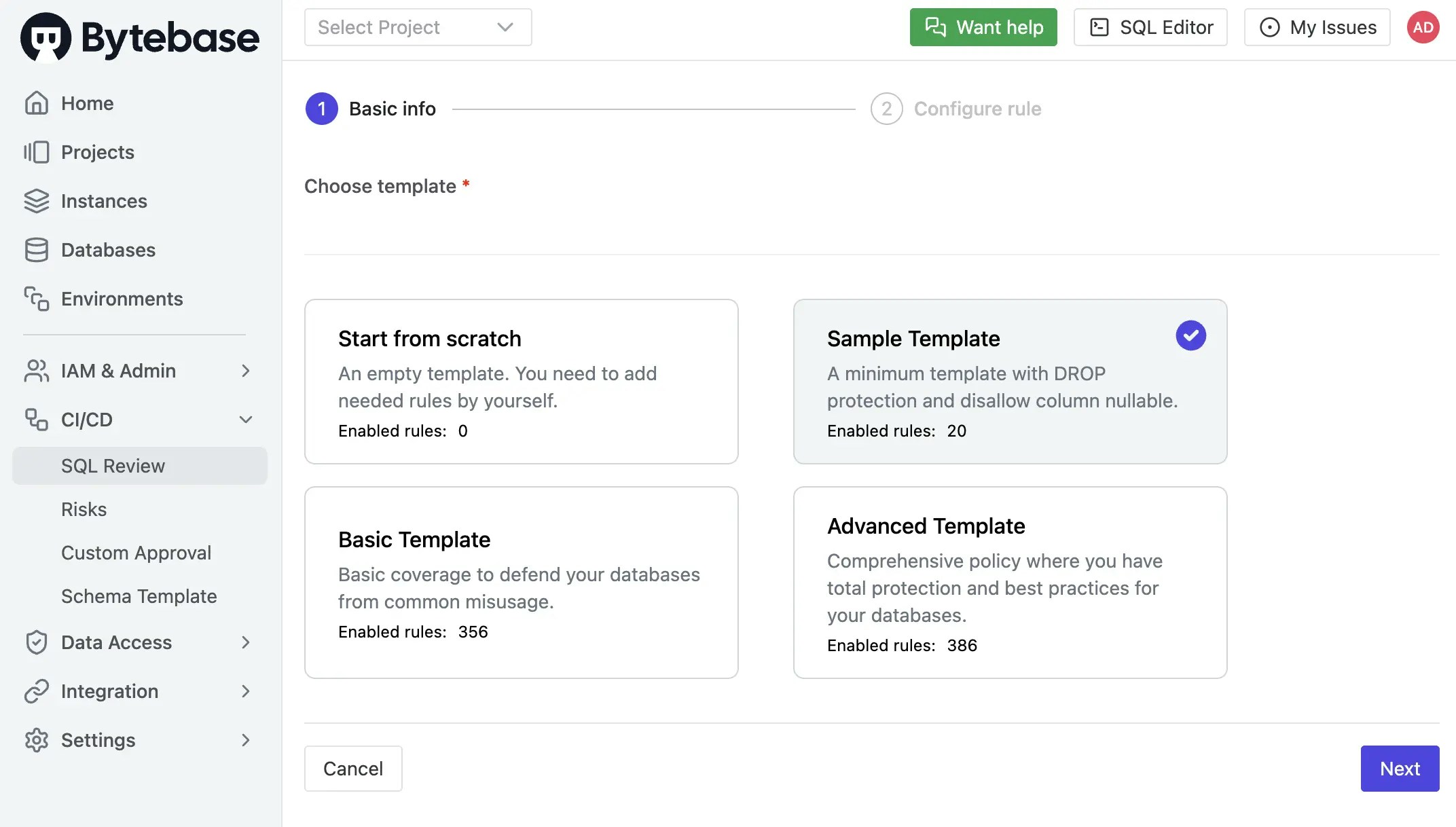
-
Select
Prodenvironment as the attached resources and click Confirm. Now the SQL review is enabled for theProdenvironment.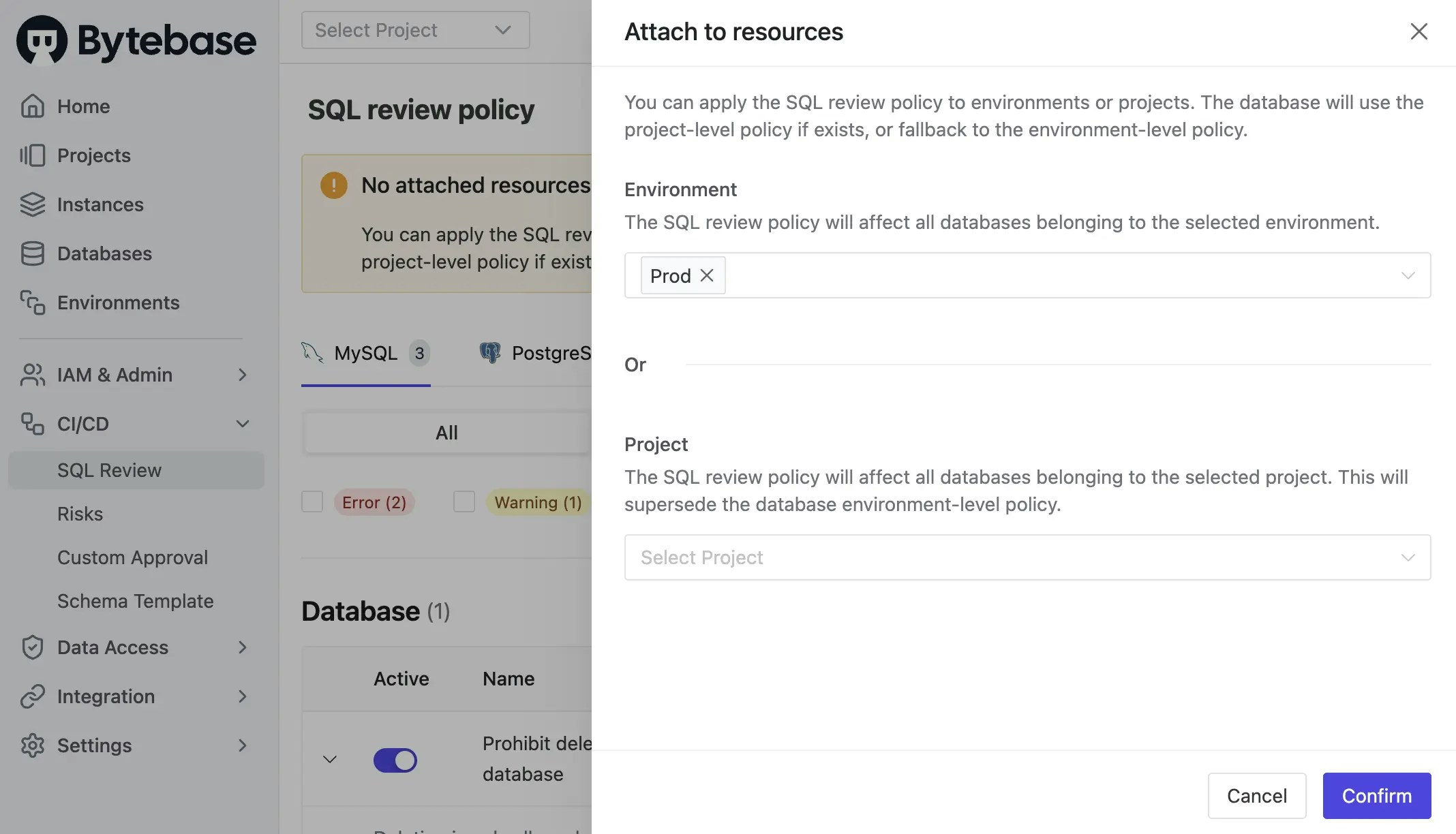
Prod environment as above. In this demo, we would switch to enable it for Test to fit the following GitLab CI workflow.
Step 4 - Copy the Example Repository and Configure Variables
-
Create a new repository and copy the configuration files from https://gitlab.com/bytebase-sample/gitops-example. There are two ymls in this repository:
.gitlab-ci.yml: The CI pipeline for the repository which includes the SQL review and release creation.bytebase-review.yml: Lint the SQL migration files after the MR is created.bytebase-rollout.yml: Create a release in Bytebase after the MR is merged to themainbranch.
-
Go into
bytebase-review.ymlandbytebase-rollout.yml. In theenvsection, replace the variable values with your own and commit the changes.- BYTEBASE_URL: Your Bytebase instance URL (e.g.,
https://bytebase.your-company.comor your Bytebase Cloud URL) - BYTEBASE_SERVICE_ACCOUNT:
api-example@service.bytebase.com(the service account you created in the previous step) - BYTEBASE_SERVICE_ACCOUNT_SECRET: the password of the service account
- BYTEBASE_URL: Your Bytebase instance URL (e.g.,
bytebase-rollout.yml, pay attention to BYTEBASE_TARGETS in deploy-to-test stage. You should put all the databases including both Test and Prod environments. NOT ONLY the Test database.
Step 5 - Create the migration files
To create migration files to trigger release creation, the files have to match the following pattern:- A migration file should start with digits, which is also its version. e.g.
202505121650_create_table_t1.sql. - A migration file may end with
ddlordmlto indicate its change type. If it doesn’t end with any of the two, its change type is DDL by default.
-
Within your forked repository, create the following migration files under
migrationdirectory:- 202505121650_create_table_t1.sql
-
Commit to a new branch and create a merge request, the
sql-reviewpipeline will be triggered. There will be a warning in the SQL review result.
-
According to the SQL review result, you can do some changes to the SQL files and push to the branch. Then you should see the SQL review has passed. There are no warnings in the SQL review result.
-
When the SQL review is passed, you can merge the merge request. The
releasepipeline will be triggered to create a release in Bytebase and then deploy automatically. -
Click into the pipelines, you can see the release pipeline is triggered and passed. Click the number of the pipeline, you can see the stages.


-
If you click the
deploy-to-testand expand the logs, you can follow the links to Bytebase.
Self-hosted GitLab Considerations
Use bytebase-action in an Offline GitLab Runner
If you are self-hosting GitLab in an internal network that has no access to the public internet, your CI/CD jobs may fail with the following error: Job failed: failed to pull image "bytebase/bytebase-action:latest". Since the image cannot be pulled directly from Docker Hub, you’ll need to download it from an external machine, then transfer and load it into your internal environment manually.
-
On an external (internet-accessible) machine:
-
Transfer the
bytebase-action.tarfile to your internal server. Usescp, USB drive, or any method suitable for your setup. -
On your internal (offline) machine:
Note: docker tag step is only needed if the loaded image doesn’t already have the correct tag.
Resolve GitLab Clone Redirect in Internal Network
If your GitLab instance uses an external URL but is hosted in an internal network,bytebase-action may fail with:
clone_url in your GitLab Runner configuration to point to the internal GitLab address:

