- Part 1: Manage Environments with Terraform - Set up environments with policies
- Part 2: Manage Databases with Terraform - Register database instances
- Part 3: Manage Projects with Terraform - Organize databases into projects
- Part 4: Manage Bytebase Settings with Terraform - Configure workspace profile and approval policies
- Part 5: Manage SQL Review Rules with Terraform - Define SQL review policies
- Part 6: Manage Users and Groups with Terraform 👈
- Part 7: Manage Database Access Control with Terraform - Grant database permissions
- Part 8: Manage Data Masking with Terraform - Protect sensitive data
This tutorial series uses separate Terraform files for better organization. Files are numbered by tutorial part and sub-step (e.g., 1-1-env-setting.tf, 1-2-env-policy-rollout.tf for Part 1, 2-instances.tf for Part 2, etc.). Terraform automatically handles dependencies between files.
What You’ll Learn
- Create users and service accounts for team members
- Organize users into groups for easier management
- Understand the difference between users and service accounts
- Prepare for setting up permissions in the next tutorial
Prerequisites
Before starting this tutorial, ensure you have:- Completed Part 5: Manage SQL Review Rules with Terraform
- Bytebase running with service account configured
- Your Terraform files from the previous tutorials
Setup
From the previous tutorials, you should have:- Bytebase workspaces and projects configured
- Workspace settings and approval flows set up
- Service account with
Workspace Adminrole
Understanding User Management in Bytebase
Bytebase adopts Identity and Access Management (IAM) system with:- Users: Individual accounts for team members
- Service Accounts: Automated accounts for API/Terraform access
- Groups: Collections of users for easier permission management
Configure Users and Groups
Step 1 - Create Users and Service Accounts
| Terraform resource | bytebase_user |
| Sample file | 6-1-users.tf |
6-1-users.tf to define your team structure:
6-1-users.tf
Step 2 - Apply User Configuration
Step 3 - Create Groups
Groups simplify permission management by allowing you to assign roles to multiple users at once.| Terraform resource | bytebase_group |
| Sample file | 6-2-groups.tf |
6-2-groups.tf file:
6-2-groups.tf
Step 4 - Apply Complete Configuration
Step 5 - Verify in Bytebase
-
Go to IAM & Admin > Users & Groups to see all users:
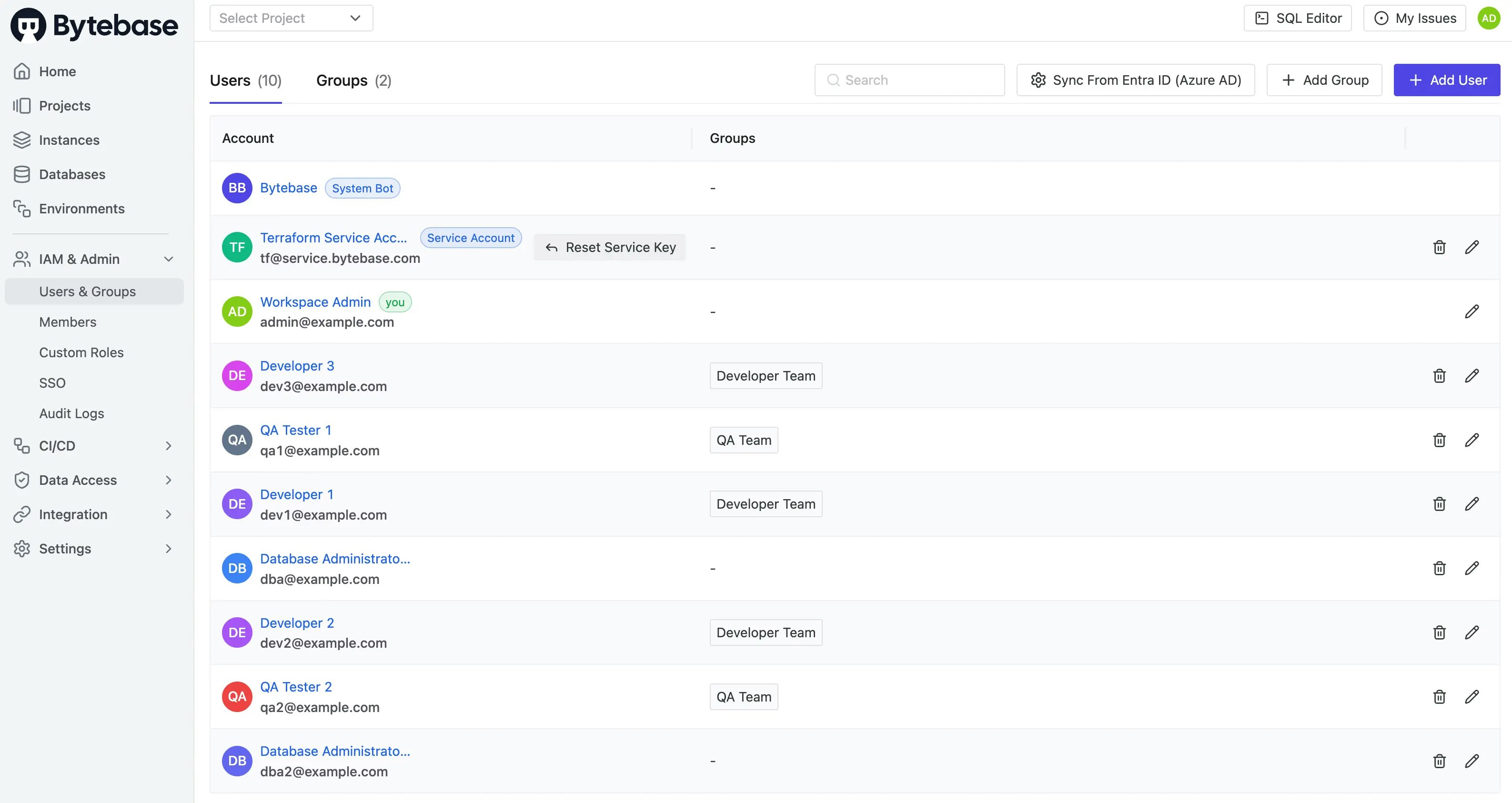
-
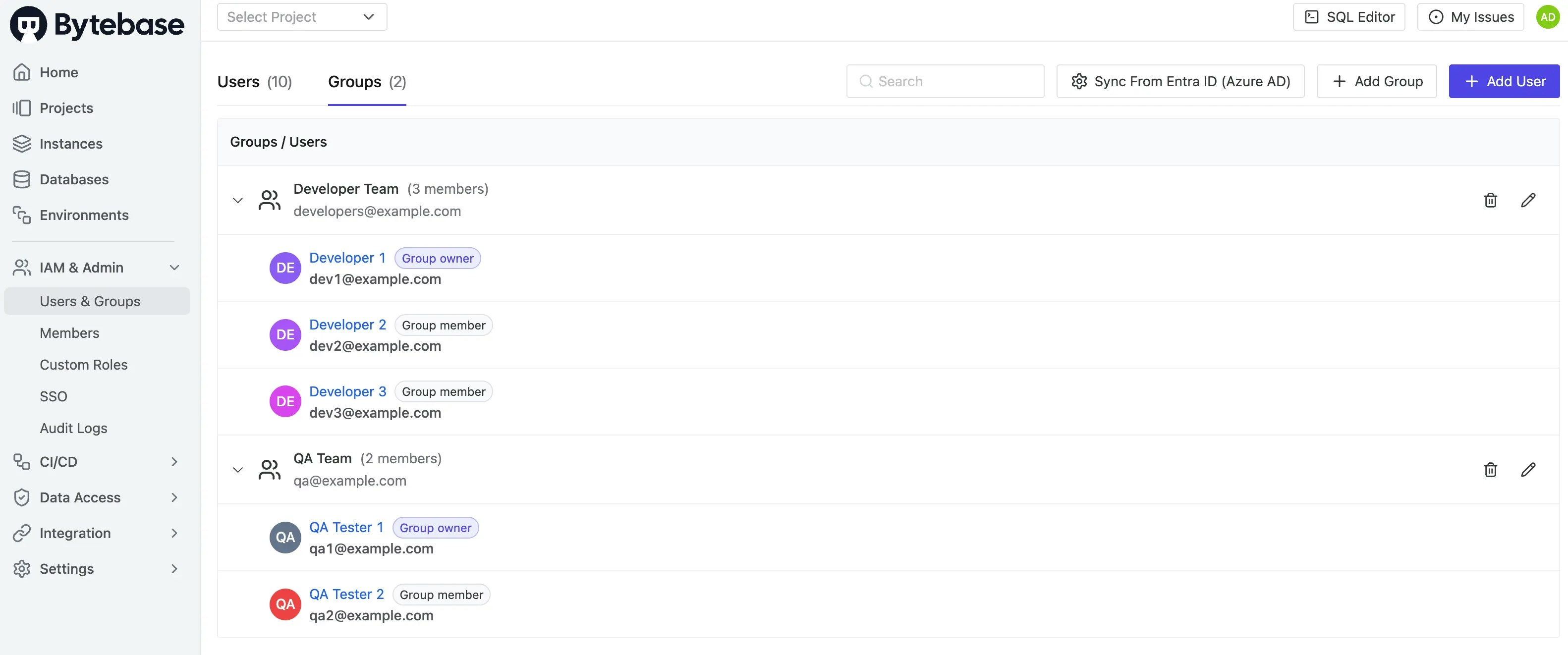
Click the Groups tab to verify groups:
- Developer Team: 3 members (dev1 as owner, dev2 and dev3 as members)
- QA Team: 2 members (qa1 as owner, qa2 as member)
Key Points
- User Types: Regular users (
USER) for team members, service accounts (SERVICE_ACCOUNT) for API/automation - Group Roles: Each group has owners (manage membership) and members (inherit permissions)
- Organization: Groups simplify permission management - assign roles to groups instead of individual users

