- Part 1: Manage Environments with Terraform - Set up environments with policies
- Part 2: Manage Databases with Terraform - Register database instances
- Part 3: Manage Projects with Terraform - Organize databases into projects
- Part 4: Manage Bytebase Settings with Terraform - Configure workspace profile and approval policies
- Part 5: Manage SQL Review Rules with Terraform 👈
- Part 6: Manage Users and Groups with Terraform - Configure users and groups
- Part 7: Manage Database Access Control with Terraform - Grant database permissions
- Part 8: Manage Data Masking with Terraform - Protect sensitive data
This tutorial series uses separate Terraform files for better organization. Files are numbered by tutorial part and sub-step (e.g., 1-1-env-setting.tf, 1-2-env-policy-rollout.tf for Part 1, 2-instances.tf for Part 2, etc.). Terraform automatically handles dependencies between files.
What You’ll Learn
In this tutorial, you’ll learn how to:- Set up automated SQL review rules to maintain schema standards
- Implement naming conventions and structural requirements across your databases
- Configure severity levels (
ERROR,WARNING) to control validation strictness - Apply review policies to specific environments for targeted governance
- Test your SQL review rules to ensure they work as intended
Prerequisites
Before starting this tutorial, ensure you have:- Completed Part 4: Manage Bytebase Settings with Terraform
- Bytebase running with service account configured
- Your Terraform files from the previous tutorials
Setup
From the previous tutorials, you should have:- Bytebase workspaces and projects configured
- Environments (
TestandProd) set up - Workspace settings and approval flows configured
Configure SQL Review Rules
SQL Review rules automatically validate SQL statements against predefined standards, ensuring code quality and schema consistency before changes enter the approval workflow.| Terraform resource | bytebase_review_config |
| Sample file | 5-sql-review.tf |
Step 1 - Create Review Configuration
The examples below demonstrate some SQL Review rules. For a comprehensive list of available rules and their configuration options, refer to the Terraform provider resource documentation linked above.
5-sql-review.tf with the SQL review configuration:
5-sql-review.tf
The configuration above applies SQL Review rules specifically to the
Prod environment. Alternatively, you can scope rules to a specific project by using bytebase_project.sample_project.name in the resources attribute.Step 2 - Apply Configuration
Step 3 - Verify in Bytebase
-
Navigate to CI/CD > SQL Review in the left sidebar. You should see
Sample SQL Review Configlisted, showing that it’s applied to theProdenvironment.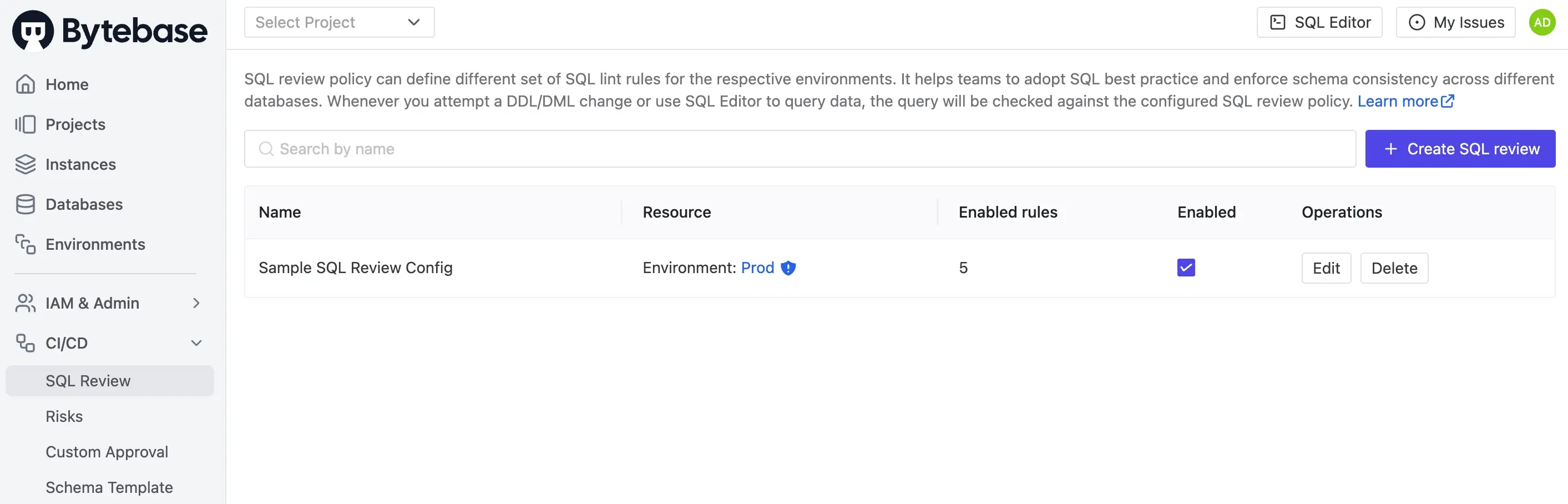
-
Click on the configuration to examine the rules you’ve defined.
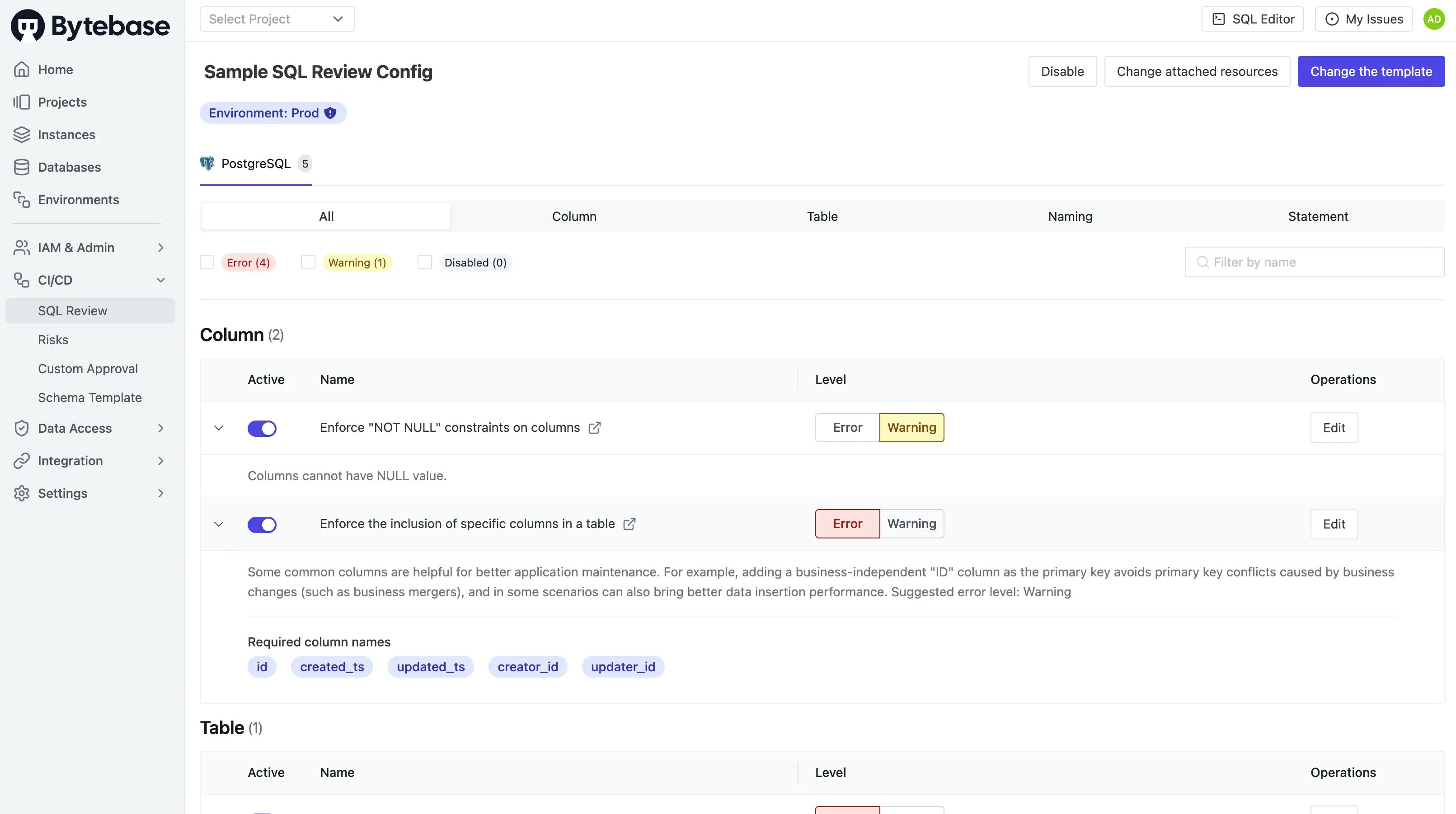
Understanding SQL Review Rules
SQL Review rules are organized into categories based on what they validate:1. Column Rules
- column.no-null: Issues warnings about nullable columns to promote data integrity and prevent null-related errors
- column.required: Mandates the presence of essential columns (ID, timestamps, audit fields) to ensure consistent table structure
2. Table Rules
- table.require-pk: Guarantees that every table includes a primary key, which is crucial for data integrity, replication, and query performance
3. Naming Rules
- naming.column: Enforces consistent lowercase snake_case naming conventions across your database schema, improving readability and maintainability
4. Statement Rules
- statement.maximum-limit-value: Prevents potentially harmful SELECT queries by requiring appropriate LIMIT clauses, protecting against performance degradation
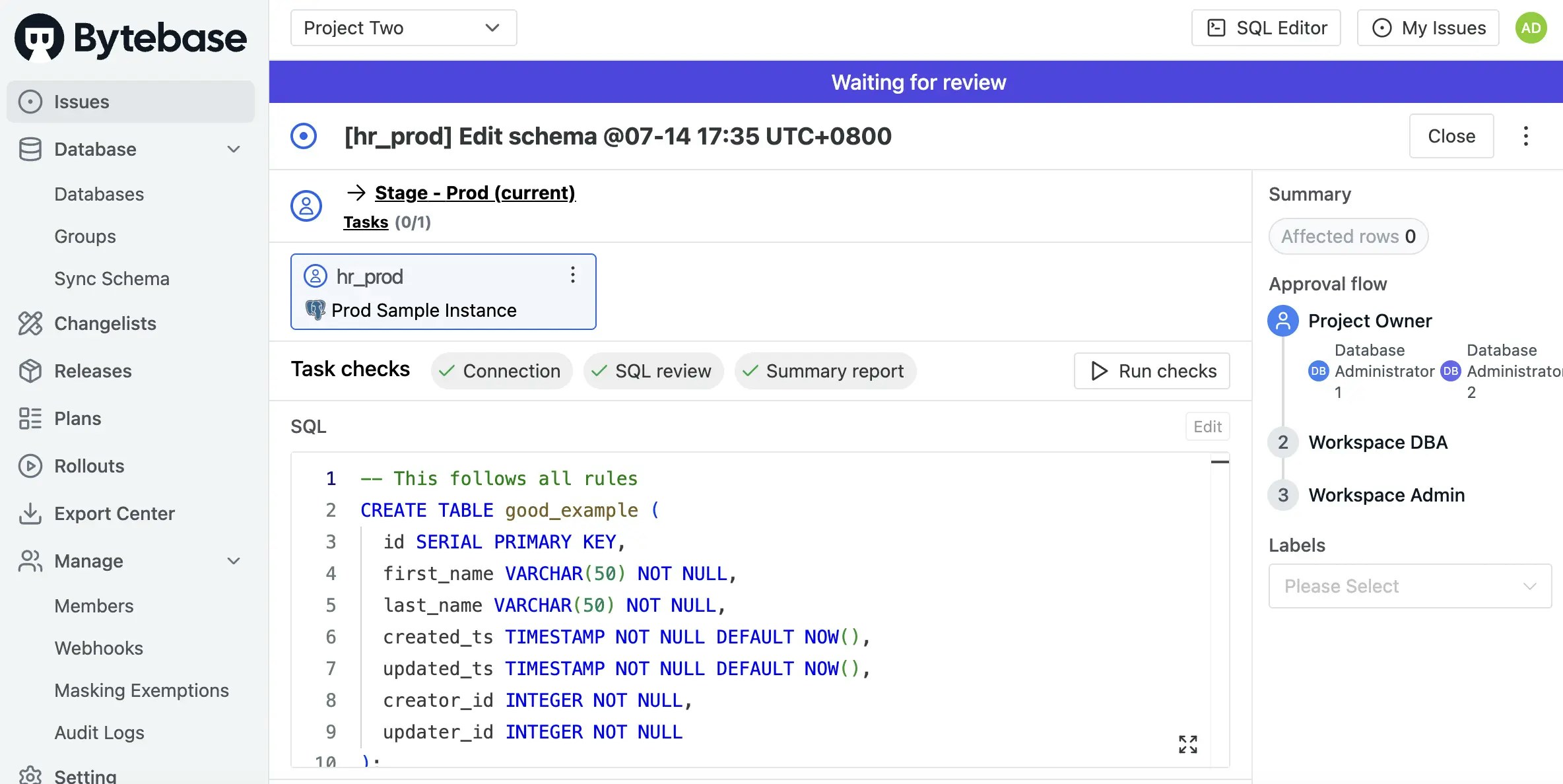
Step 4 - Test SQL Review
Let’s validate that your SQL Review rules are working by testing them with some sample SQL:- Navigate to Project Two, then click Database > Databases in the left sidebar.
-
Select the
hr_proddatabase and click Edit Schema. -
Create a table that intentionally violates multiple rules:
Expected violations:
- ❌ Column naming convention violation (should be
first_name,last_name) - ❌ Missing required audit columns (
id,created_ts,updated_ts,creator_id,updater_id) - ❌ No primary key defined
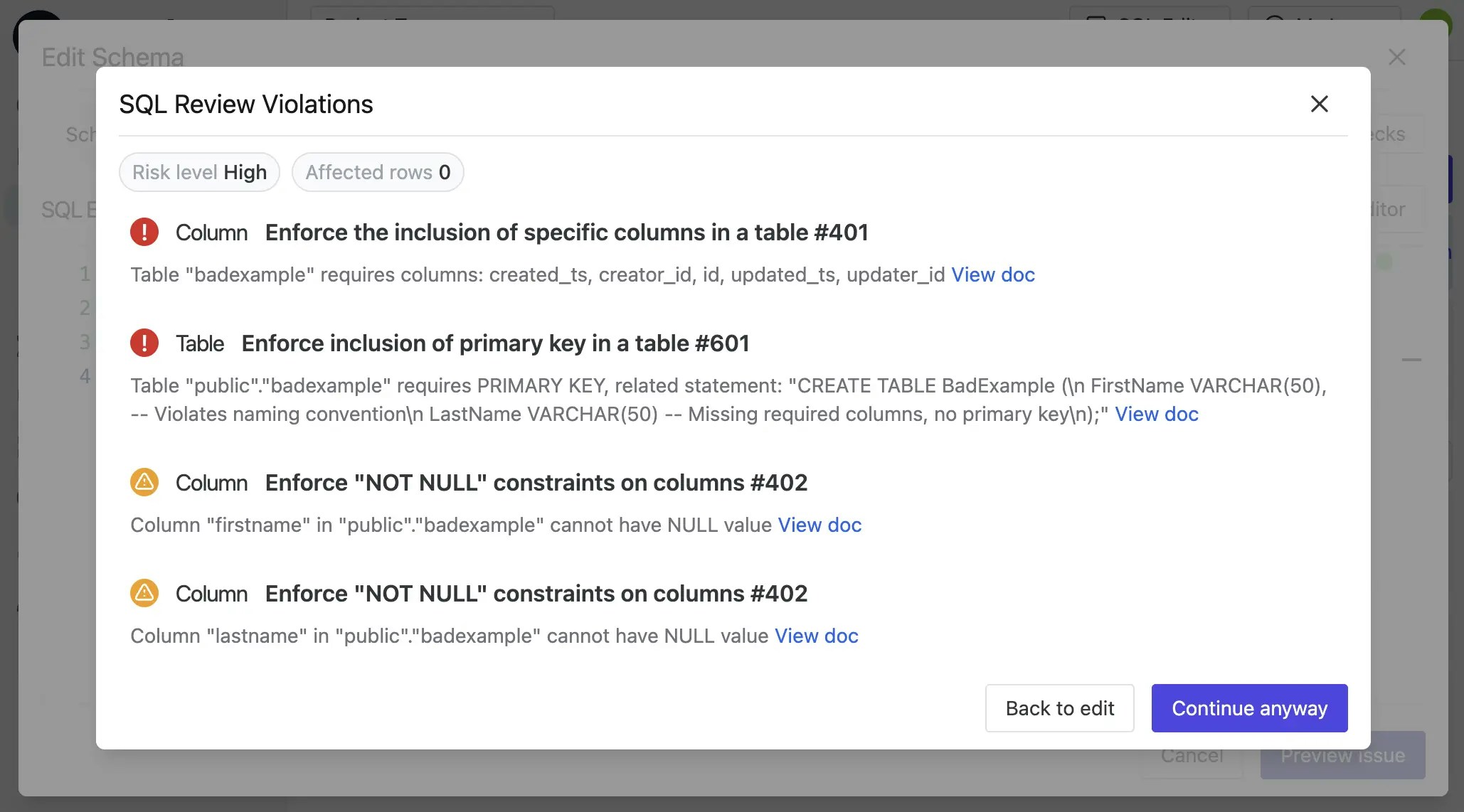
- ❌ Column naming convention violation (should be
-
Even if you proceed to create an issue, the SQL Review violations will be prominently displayed with error indicators.
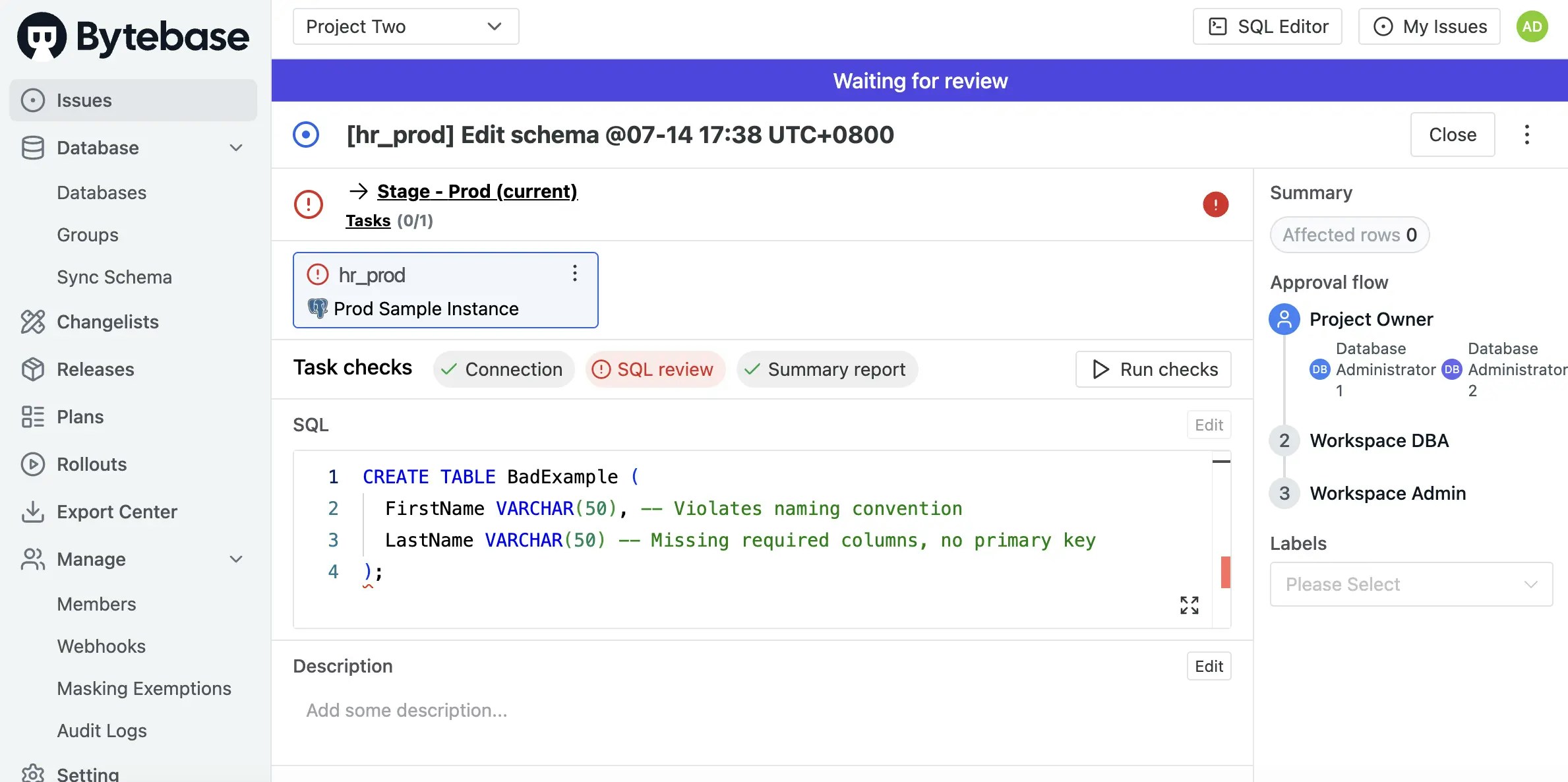
-
Now try creating a compliant table that follows all your rules:
Expected result:
- ✅ All SQL review rules pass successfully
Advanced Configuration
Targeting Multiple Environments
To apply rules to multiple environments:Engine-Specific Rules
Different rules for different database engines:Key Points
- Rule Levels:
ERROR: Blocks SQL statement execution, preventing non-compliant changes from proceedingWARNING: Permits execution while alerting users to potential issues, useful for gradual policy adoption
- Engine Specificity: Rules can be tailored to specific database engines (PostgreSQL, MySQL, Oracle, etc.) to accommodate platform differences
- Environment Scoping: Apply stricter rules to production while allowing more flexibility in development and testing environments
- Payload Configuration: Complex rules utilize JSON payloads for detailed configuration (regex patterns, value lists, thresholds)
- Implementation Strategy: Begin with
WARNINGlevel rules to familiarize teams with standards, then gradually transition toERRORlevel for enforcement

