- Part 1: Manage Environments with Terraform - Set up environments with policies
- Part 2: Manage Databases with Terraform - Register database instances
- Part 3: Manage Projects with Terraform - Organize databases into projects
- Part 4: Manage General Settings with Terraform 👈
- Part 5: Manage SQL Review Rules with Terraform - Define SQL review policies
- Part 6: Manage Users and Groups with Terraform - Configure users and groups
- Part 7: Manage Database Access Control with Terraform - Grant database permissions
- Part 8: Manage Data Masking with Terraform - Protect sensitive data
This tutorial series uses separate Terraform files for better organization. Files are numbered by tutorial part and sub-step (e.g., 1-1-env-setting.tf, 1-2-env-policy-rollout.tf for Part 1, 2-instances.tf for Part 2, etc.). Terraform automatically handles dependencies between files.
This tutorial configures workspace-level settings that apply to all projects and environments in
your Bytebase workspace.
What You’ll Learn
- Configure workspace profile settings including signup controls and external URL
- Define risk policies to automatically assess database operations
- Create multi-step and risk-based approval flows for database changes
Prerequisites
Before starting this tutorial, ensure you have:- Completed Part 3: Manage Projects with Terraform
- Bytebase running with service account configured
- Your Terraform files from the previous tutorials
Setup
From the previous tutorials, you should have:- Bytebase workspaces and projects configured
- Service account with Workspace Admin role
- Your Terraform files ready for additional configurations
Configure General Settings
Step 1 - Workspace Profile Configuration
| Terraform resource | bytebase_setting |
| Sample file | 4-1-workspace-profile.tf |
4-1-workspace-profile.tf with the workspace profile settings:
4-1-workspace-profile.tf
- Disables public signup for security
- Restricts users to specific email domains
- Sets your Bytebase workspace’s external URL
Step 2 - Risk Management Policies
| Terraform resource | bytebase_risk |
| Sample file | 4-2-risk.tf |
4-2-risk.tf with risk policies to assess the database operations’ risk level:
4-2-risk.tf
- 100 (LOW).
- 200 (MODERATE): DML operations in production affecting 100+ rows
- 300 (HIGH): All DDL operations in production
Step 3 - Approval Flow Settings
| Terraform resource | bytebase_setting |
| Sample file | 4-3-approval-flow.tf |
4-3-approval-flow.tf with approval flow configuration that requires multiple approvals for risky operations:
4-3-approval-flow.tf
- DML operations with MODERATE risk level
- DDL operations with HIGH risk level
Step 4 - Apply Configuration
Step 5 - Verify Configuration
Workspace Profile Settings
- Go to Settings > General to verify workspace profile settings.
- Log out and try to signup which should be disabled.
- Visit the external URL to verify it is set.
Risk Policies
-
Go to CI/CD > Risks to view risk policies.
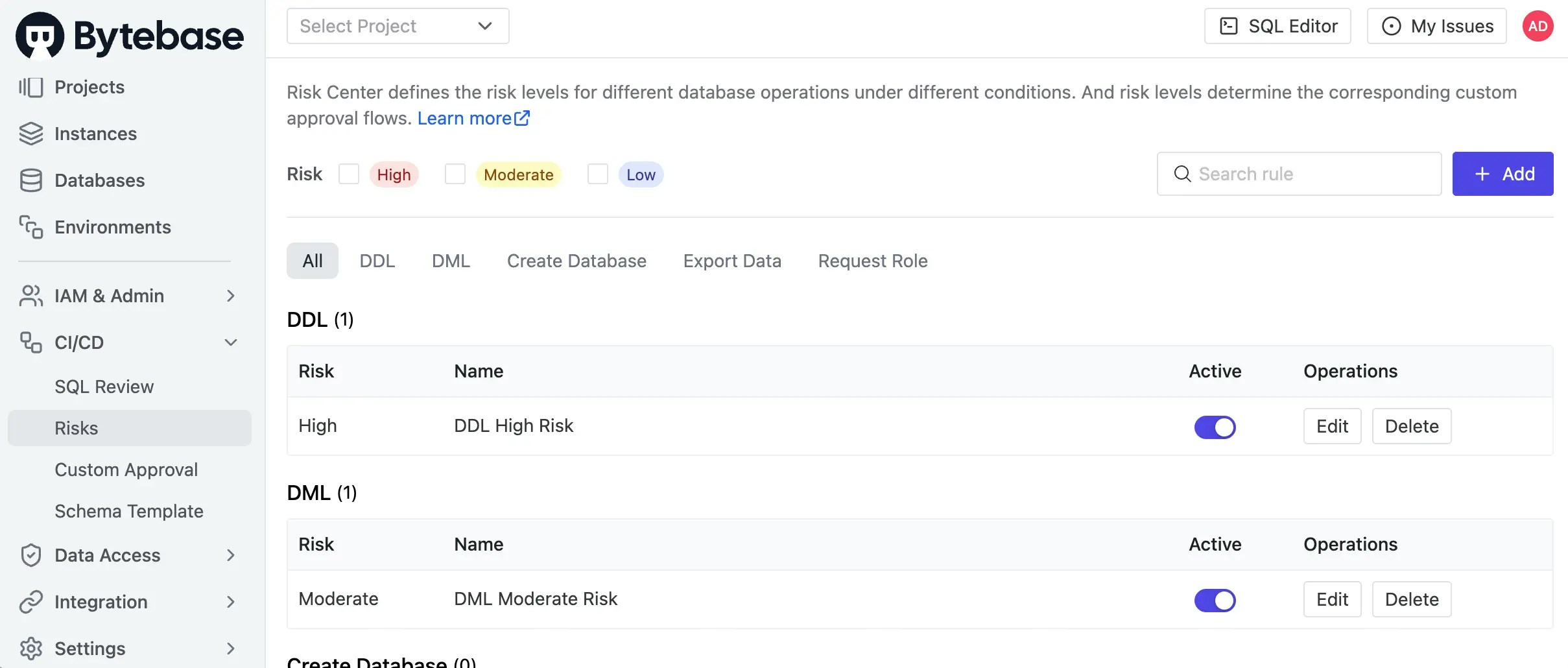
- You should see both “DML Moderate Risk” and “DDL High Risk” policies active.
Approval Flows
-
Go to CI/CD > Custom Approval to see the approval flow.
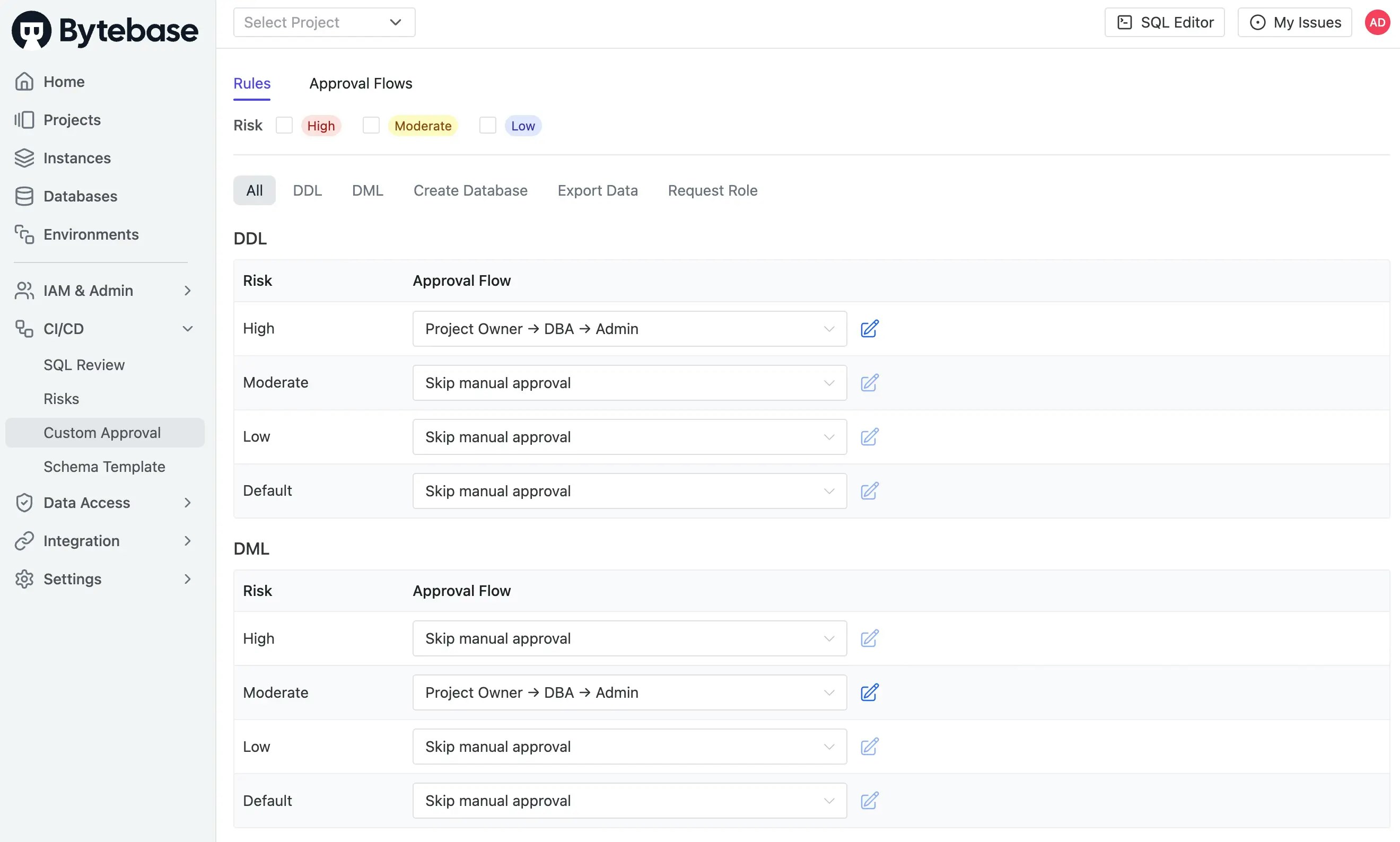
-
Verify the
Project Owner → DBA → Adminflow is configured.
Test the Flow
-
Go to
Project Two, click Database > Databases on the left sidebar. -
Check
hr_prod, click Edit Schema, add a new tablet0. -
After creating the issue, you should see:
- Risk level:
DDL High - Approval flow:
Project Owner → DBA → Admin
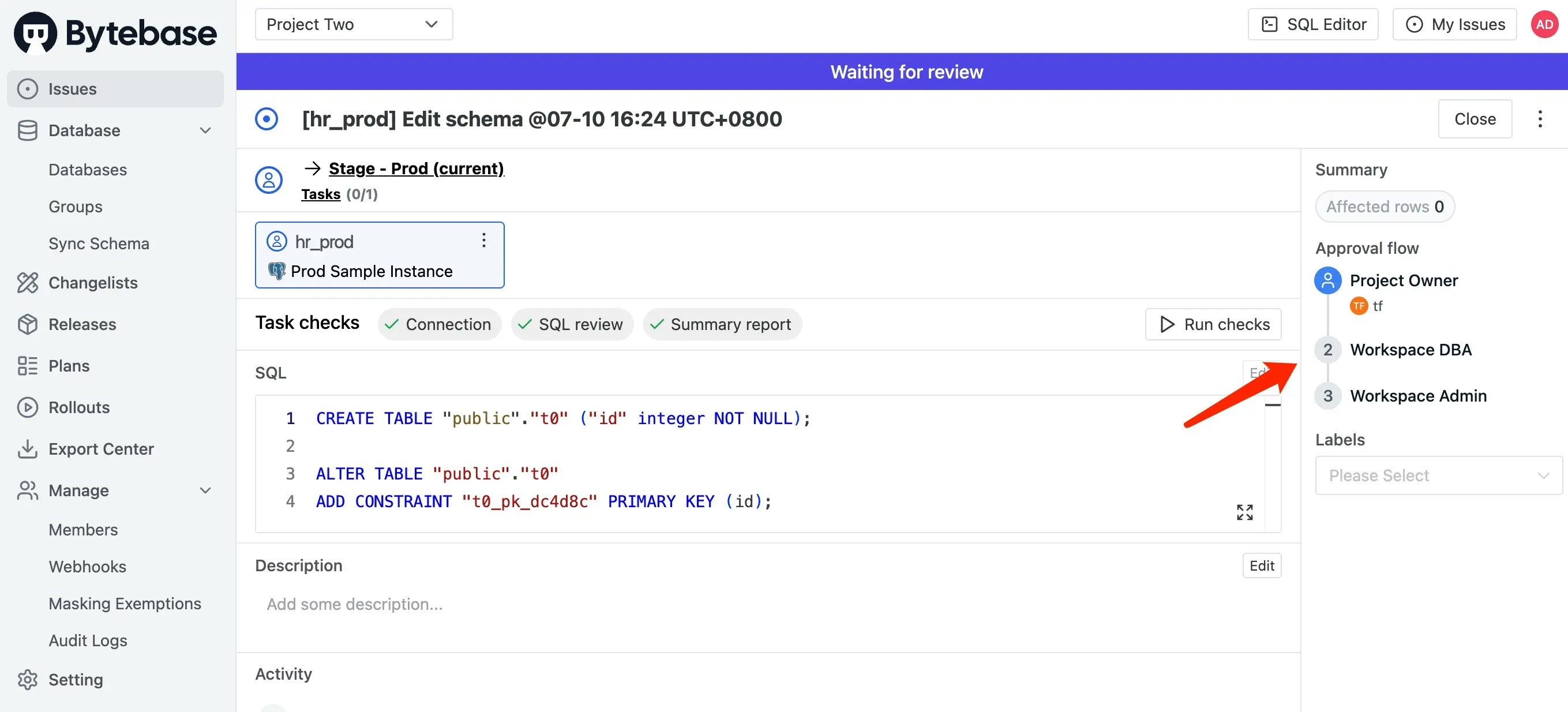
- Risk level:
Key Points
- Workspace Profile: Controls signup, domain restrictions, and external URL for your entire Bytebase workspace
- Risk Policies: Automatically assess database operations based on conditions like environment and affected rows
- Approval Flows: Define multi-step approval processes that trigger based on risk levels
- Integration: Risk policies and approval flows work together to ensure proper governance for database changes

